Oman , Salalah |
|||
|---|---|---|---|

|
CERTIFIED INFORMATION SECURITY MANAGERFive years of experience with audit, IT systems, and security of information systems; systems administration experience; familiarity with TCP/IP; and an understanding of UNIX, Linux, and Windows. This advanced course als ... |
|
Register |

|
JNCIE-SEC BOOT CAMPThis five-day course is designed to serve as the ultimate preparation for the Juniper Networks Certified Internet Expert—Security (JNCIE-SEC) exam. The course focuses on caveats and tips useful for potential test candida ... |
|
Register |

|
CompTIA Pentest +As organizations scramble to protect themselves and their customers against privacy or security breaches, the ability to conduct penetration testing is an emerging skill set that is becoming ever more valuable to the org ... |
|
Register |

|
SYMANTEC DATA CENTER SECURITY SERVER ADVANCED 6.7 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec Data Center Server Advanced 6.7 Diagnostics and Troubleshooting course is designed for the IT security management professional tasked with troubleshooting Data Center Security Server Advanced (SDCSSA). Stud ... |
|
Register |

|
SYMANTEC IT MANAGEMENT SUITE 8.1 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec IT Management Suite 8.1 Diagnostics and Troubleshooting course is designed for professionals tasked with maintaining and utilizing a Symantec IT Management Suite (ITMS) implementation in their organizations. ... |
|
Register |

|
EC-COUNCIL CERTIFIED NETWORK DEFENDERCertified Network Defender (CND) is a vendor-neutral, hands-on, instructor-led comprehensive network security certification training program. It is a skills-based, lab intensive program based on a job-task analysis and c ... |
|
Register |
|
MASTER CLASS ISO 27001 IMPLEMENTATIONThis five-day intensive course enables the participants to develop the expertise to support an organization in implementing and managing an Information Security Management System (ISMS) as specified in ISO/IEC 27001:2013 ... |
|
Register |

|
IBM DIRECTORY SERVER 6.4 FUNDAMENTALSThis course describes the processes, procedures, and practices necessary to configure and administer IBM Directory Server. During the hand-on exercises, students will perform basic Directory Server configuration, setup r ... |
|
Register |
.jpg)
|
RED HAT IDENTITY MANAGEMENT AND ACTIVE DIRECTORY INTEGRATION WITH EXAM (EX362)This course teaches you skills on the most requested Red Hat Identity Management (IdM) capabilities, including Active Directory trusts, multi-product federation, configuration management with Ansible, integrated certific ... |
|
Register |

|
PERFORMANCE TUNING AND OPTIMIZING SQL DATABASESThis four-day instructor-led course provides students who manage and maintain SQL Server databases with the knowledge and skills to performance tune and optimize their databases. |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 15.5 ADMINISTRATIONThe Symantec Data Loss Prevention 15.5 Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands‐on labs inc ... |
|
Register |
.jpg)
|
FIREWALL 8.1: TROUBLESHOOTING (EDU-330)Successful completion of this three-day, instructor-led course will enhance the participant’s understanding of how to troubleshoot the full line of Palo Alto Networks® next-generation firewalls. Participants will have o ... |
|
Register |

|
IMPLEMENTING CISCO NETWORK SECURITY V3.0This is a five-day instructor-led course that focuses on the design, implementation and monitoring of a comprehensive security policy, using Cisco IOS security features and technologies. All IOS examples and hands on exp ... |
|
Register |

|
EC - COUNCIL CERTIFIED SECURE PROGRAMMERSoftware defects, bugs, and flaws in the logic of the program are consistently the cause for software vulnerabilities. Analysis by software security professionals has proven that most vulnerabilities are due to errors i ... |
|
Register |

|
IMPLEMENTING AND CONFIGURING CISCO IDENTITY SERVICES ENGINEThe Implementing and Configuring Cisco Identity Services Engine course shows you how to deploy and use Cisco Identity Services Engine (ISE) v2.4, an identity and access control policy platform that simplifies the deliver ... |
|
Register |

|
BLUE COAT PACKET SHAPER PROFESSIONALBlue Coat Certified Packet Shaper Administrator (BCPSA) certification or waiver exam; student should have practical experience with the Packet Shaper appliance in the field with a solid understanding of networking and ge ... |
|
Register |

|
IMPLEMENTING CISCO CYBERSECURITY OPERATIONSThis is the second course in Cisco's CCNA Cyber Ops Curriculum and is designed to provide students with an understanding of how a Security Operations Center (SOC) functions and the knowledge required in this environment. ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS SECURITY PROFESSIONALThe Official (ISC)2® CISSP® CBK® Review Seminar is the most comprehensive, complete review of information systems security concepts and industry best practices, and the only review course endorsed by (ISC)2. Review Semin ... |
|
Register |

|
IMPLEMENTING CISCO EDGE NETWORK SECURITY SOLUTIONSThis course has been designed to provide students with the knowledge and skills required to implement and manage security on Cisco ASA firewalls, Cisco Routers with the firewall feature set and Cisco Switches. Students w ... |
|
Register |

|
JUNOS SPACE-SECURITY DIRECTORThis two-day course is designed to provide students with the knowledge required to manage the Junos Space Security Director application and manage devices with that application. Students will gain in-depth knowledge of h ... |
|
Register |
|
CITRIX ENTERPRISE SECURITY SOLUTIONSLearn to secure your Citrix environment in this hands-on course that encompasses the core Citrix technologies, including Citrix Virtual Apps and Desktops, ADC, Endpoint Management, Content Collaboration and Citrix Cloud. ... |
|
Register |

|
MASTERCLASS: PEN TESTING AND SECURING MOBILE AND WEB APPLICATIONSThe course teaches mobile and web application security concepts, including the techniques on how to attack and how to respond with an appropriate countermeasure implementation. Our course has been developed around profes ... |
|
Register |

|
WEB SECURITY SERVICE 6.10 DIAGNOSTICS AND TROUBLESHOOTINGThe WSS Diagnostics and Troubleshooting course is intended for IT professionals who will be diagnosing and troubleshooting the Symantec Web Security Service (WSS). |
|
Register |

|
BLUE COAT CERTIFIED PROXY PROFESSIONALIn the Blue Coat Certified Proxy Professional (BCCPP) course, you will learn to configure your Blue Coat Proxy appliance for high availability and multi-site deployments, advance policy features, web content control, P2P ... |
|
Register |
|
CONFIGURING AND DEPLOYING A PRIVATE CLOUDThis course equips students with the skills they require to configure and deploy a cloud using Microsoft System Center 2012 R2. Using hands-on labs, students learn the following: - Produce a high-level design that acc ... |
|
Register |
.jpg)
|
PALO ALTO NETWORKS® TRAPS™ ADVANCED ENDPOINT PROTECTION (PAN-EDU-281)This instructor-led course teaches strategies in defense against advanced threats. Successful completion of this course enables administrators to better understand the threat landscape. Students will learn the use of Pal ... |
|
Register |

|
IBM QRADAR SIEM FOUNDATIONSIBM QRadar SIEM provides deep visibility into network, user, and application activity. It provides collection, normalization, correlation, and secure storage of events, flows, asset profiles, and vulnerabilities. QRadar ... |
|
Register |

|
RED TEAM VS BLUE TEAM CYBERWAR CHALLENGETwo Teams, two different approaches, Red Team vs Blue Team Cyberwar Challenge! The cyber kill chain - reconnaissance, attack planning and delivery, system exploitation, privilege escalation and lateral movement, anomalie ... |
|
Register |

|
SYMANTEC WEB SECURITY SERVICE CORE ADMINISTRATION R1The Web Security Service Core Administration course is intended for IT professionals who will be installing, configuring or administering the Symantec Web Security Service (WSS). |
|
Register |

|
CYBER SEC FIRST RESPONDER: THREAT DETECTION AND RESPONSEThis course covers the duties of those who are responsible for monitoring and detecting security incidents in information systems and networks, and for executing a proper response to such incidents. Depending on the size ... |
|
Register |

|
JUNOS SPACE-SECURITY DIRECTORThis two-day course is designed to provide students with the knowledge required to manage the Junos Space Security Director application and manage devices with that application. Students will gain in-depth knowledge of h ... |
|
Register |

|
TREND MICRO APEX ONE TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro Apex One™. This course details basic architecture, protection functionality, deployment scenarios, and troubleshooting. Through hands-on labs, participants practice c ... |
|
Register |
|
SYMANTEC PROXY SG V6.6: ADVANCED ADMINISTRATIONThe Proxy SG v6.6 Advanced Administration course is intended for IT professionals who wish to learn to master the advanced features of Proxy SG. |
|
Register |

|
SECURING NETWORKS WITH FIREPOWER THREAT DEFENSE NGFWThe Securing Networks with Cisco Firepower Threat Defense NGFW (FIREPOWER200) course demonstrates the powerful features of Cisco Firepower Threat Defense, including VPN configuration, traffic control, NAT configuration, ... |
|
Register |
.jpg)
|
RED HAT SECURITY: LINUX IN PHYSICAL, VIRTUAL, AND CLOUD WITH EXAM (EX415)Maintaining security of computing systems is a process of managing risk through the implementation of processes and standards backed by technologies and tools. In this course, you will learn about resources that can be u ... |
|
Register |

|
IMPLEMENTING AND MANAGING WINDOWS 10This course is designed to provide students with the knowledge and skills required to install and configure Windows 10 desktops and devices in a Windows Server domain corporate environment. These skills include learning ... |
|
Register |
.jpg)
|
EC-COUNCIL CERTIFIED SOC ANALYST (CSA)The Certified SOC Analyst (CSA) program is the first step to joining a security operations center (SOC). It is engineered for current and aspiring Tier I and Tier II SOC analysts to achieve proficiency in performing entr ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.5: ADMINISTRATIONThe Symantec Messaging Gateway 10.5: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This three-day, instructor-led, hands-on cl ... |
|
Register |

|
SYMANTEC CONTROL COMPLIANCE SUITE VULNERABILITY MANAGER 12.0 ADMINISTRATIONThe Symantec Control Compliance Suite Vulnerability Manager (CCS-VM) 12.0 Administration Training is designed for the IT security professional tasked with installation, administering, monitoring and reporting on CCS-VM 1 ... |
|
Register |
|
CLIENT MANAGEMENT SUITE 8.1 ADMINISTRATIONThe Client Management Suite 8.1 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |

|
DEV SEC OPS ENGINEERINGA Dev Sec Ops Engineer is an IT Security professional who is skilled at “security as code” with the intent of making security and compliance consumable as a service. A Dev Sec Ops Engineer uses data and security science ... |
|
Register |

|
WORKSHOP: WINDOWS SERVER 2019Learn about the new enhanced capabilities of the Windows 2019 starting from server virtualization, storage, software-defined networking, server management and automation, web and application platform, access to informati ... |
|
Register |

|
ADVANCED JUNOS SECURITYThis five-day course, which is designed to build off the current Junos Security (JSEC) offering, delves deeper into Junos security and next-generation security features. Through demonstrations and hands-on labs, you will ... |
|
Register |

|
CISCO ASA EXPRESS SECURITY 1.5This course has been designed to provide an understanding of Cisco's ASA solution portfolio. Students will learn how to successfully configure various aspects of the Cisco ASA components including Cisco ASA firewall feat ... |
|
Register |

|
CERTIFIED SECURE COMPUTER USER - AWARENESS TRAININGThe purpose of the CSCU training program is to provide individuals with the necessary knowledge and skills to protect their information assets. This class will immerse students into an interactive environment where they ... |
|
Register |

|
JNCIE-SEC BOOT CAMPThis five-day course is designed to serve as the ultimate preparation for the Juniper Networks Certified Internet Expert—Security (JNCIE-SEC) exam. The course focuses on caveats and tips useful for potential test candida ... |
|
Register |
|
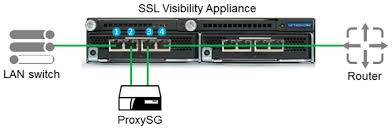
SYMANTEC SSL VISIBILITY 4.3 ADMINISTRATIONThe SSL Visibility 4.3 administration course enables you to plan, implement, configure and managed your SSLV appliance(s). This is a lecture-only course, there will be no hands-on access to an SSLV appliance during the c ... |
|
Register |
|
BLUE COAT CERTIFIED SECURITY ANALYTICS PROFESSIONALThe Blue Coat Certified Security Analytics Professional (BCSAP) course designed for participants who want to learn how to use the Blue Coat Security Analytics platform to perform virtually any type of network-based monit ... |
|
Register |

|
SYMANTEC CLOUD SOC ADMINISTRATION R2The Cloud SOC R2 Administration course provides an overview of the Cloud SOC service, covering initial setup, deployment options and service configuration. The courseware introduces each topic with an accompanying workfl ... |
|
Register |
UAE , Dubai |
|||
|---|---|---|---|

|
SYMANTEC DATA LOSS PREVENTION 14.6 ADMINISTRATIONThe Symantec Data Loss Prevention 14.X: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands-on labs i ... |
|
Register |

|
SYMANTEC CLIENT MANAGEMENT SUITE 8.5 ADMINISTRATIONThe Client Management Suite 8.5 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |

|
EC-COUNCIL CERTIFIED ENCRYPTION SPECIALISTThe EC-Council Certified Encryption Specialist (ECES) program introduces professionals and students to the field of cryptography. The participants will learn the foundations of modern symmetric and key cryptography inclu ... |
|
Register |

|
IMPLEMENTING AND MANAGING WINDOWS 10This course is designed to provide students with the knowledge and skills required to install and configure Windows 10 desktops and devices in a Windows Server domain corporate environment. These skills include learning ... |
|
Register |
 CERTIFICATION44.jpg)
|
CERTIFIED INTERNET OF THINGS PRACTITIONER (CIOTP) CERTIFICATIONThe Internet of Things (IoT) promises a wide range of benefits for industry, energy and utility companies, municipalities, healthcare, and consumers. Data can be collected in extraordinary volume and detail regarding alm ... |
|
Register |

|
CONFIGURING AND DEPLOYING A PRIVATE CLOUDThis course equips students with the skills they require to configure and deploy a cloud using Microsoft System Center 2012 R2. Using hands-on labs, students learn the following: - Produce a high-level design that acc ... |
|
Register |

|
DEPLOYING AND MANAGING WINDOWS 10 USING ENTERPRISE SERVICESThis 5-day course provides administrators with the knowledge and skills needed to deploy and manage Windows 10 desktops, devices, and applications in an enterprise environment. Students learn how to plan and implement Wi ... |
|
Register |

|
CYBERSECURITY FOUNDATIONSWhen you consider just a few of the consequences of a security breach - your proprietary information completely accessible, hefty fines for security lapses, news headlines about your company's security breach, it becomes ... |
|
Register |

|
IMPLEMENTING CISCO THREAT CONTROL SYSTEMSImplementing Cisco Threat Control Solutions is designed to provide security engineers with the knowledge and hands-on experience required to deploy Cisco’s Email Security (ESA); Web Security (CWS, WSA); Advanced Malware ... |
|
Register |

|
BLUE COAT CERTIFIED PROXY PROFESSIONALIn the Blue Coat Certified Proxy Professional (BCCPP) course, you will learn to configure your Blue Coat Proxy appliance for high availability and multi-site deployments, advance policy features, web content control, P2P ... |
|
Register |

|
IBM SECURITY IDENTITY MANAGER FOUNDATIONSThis is an instructor-led course that introduces students to the foundational skills required to install, configure, and administer IBM Security Identity Manager,. IBM Security Identity Manager can be deployed using the ... |
|
Register |

|
IBM IDENTITY GOVERNANCE AND INTELLIGENCE FOUNDATIONSIBM Identity Governance and Intelligence is an advanced identity governance system. This course provides the foundational skills necessary to operate, administer, and accomplish the major business functions and analyses ... |
|
Register |

|
ADVANCED JUNOS SECURITYThis five-day course, which is designed to build off the current Junos Security (JSEC) offering, delves deeper into Junos security and next-generation security features. Through demonstrations and hands-on labs, you will ... |
|
Register |

|
Certified Cloud Security Professional Certification PreparationAs powerful as cloud computing is for the organization, understanding its information security risks and mitigation strategies is critical. Legacy approaches are inadequate, and organizations need competent, experienced ... |
|
Register |
.jpg)
|
PANORAMA 8.1: MANAGING FIREWALLS AT SCALE (EDU-220)This course will help students to gain in-depth knowledge about how to configure and manage their Palo Alto Networks® Panorama TM management server. Upon completion of this course, administrators should be familiar with ... |
|
Register |

|
CERTIFIED CHIEF INFORMATION SECURITY OFFICEREC-Council’s CCISO Program has certified leading information security professionals around the world. A core group of high-level information security executives, the CCISO Advisory Board, contributed by forming the found ... |
|
Register |

|
Certified Threat Intelligence AnalystCertified Threat Intelligence Analyst (C|TIA) is a training and credentialing program designed and developed in collaboration with cybersecurity and threat intelligence experts across the globe to help organizations iden ... |
|
Register |
.png)
|
FIREWALL 8.1: OPTIMIZING FIREWALL THREAT PREVENTION (EDU-214)Successful completion of this four-day, instructor-led course will enhance the student’s understanding of how to better configure, manage, and monitor PAN-OS® threat prevention features. The student will get hands-on exp ... |
|
Register |

|
IMPLEMENTING CISCO UNIFIED COMMUNICATIONS SECURITYThe Implementing Cisco Unified Communications Security (UCSEC) course is designed to provide students with the necessary knowledge and skills to implement security features in a Cisco Unified Communications environment. ... |
|
Register |
.jpg)
|
LEAD AUDITOR TRAINING (IRCA CERTIFIED)This five-day intensive course enables participants to develop the expertise needed to audit an Information Security Management System (ISMS) and to manage a team of auditors by applying widely recognized audit principle ... |
|
Register |

|
MANAGING AND DEFENDING AGAINST CURRENT THREATSThis is a deep dive course on security operations: vulnerability management, anomalies detection, discovery of industry attacks and threats, understanding how compromised system or solution looks like, defining the indic ... |
|
Register |

|
DEEP SECURITY TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro™ Deep Security. This course provides information about the basic architecture, deployment scenarios, installation processes, policy configuration and administration o ... |
|
Register |

|
JUNOS INTRUSION PREVENTION SYSTEM FUNCTIONALITYThe Junos Intrusion prevention System Functionality (JIPS) course is designed to provide an introduction to the Intrusion Prevention System (IPS) feature set available on the Juniper Networks SRX Series Services Gateway. ... |
|
Register |
|
SECURITY FUNDAMENTALSIn this course, you will be introduced to security concepts for today's business and technology professionals. You will cover layered security philosophy, physical security, Internet security, and wireless security princ ... |
|
Register |
.jpg)
|
CISCO CCNA SECURITY BOOT CAMP (ACCELERATED)In this course, you will learn how to install, operate, configure, and verify a basic IPv4 and IPv6 network, including configuring a LAN switch, configuring an IP router, managing network devices. You will also learn abo ... |
|
Register |
|
Protecting Against Malware Threats with Cisco AMP for EndpointsThis lab-intensive course introduces students to the powerful features of Cisco AMP for Endpoints software. A number of step by step attack scenarios will provide an understanding of the operational uses of the product. ... |
|
Register |

|
SYMANTEC NETBACKUP 7.5: MAINTAIN AND TROUBLESHOOTThe three day Symantec Net Backup Maintain and Troubleshoot course provides the IT professional with instruction on troubleshooting Symantec NetBackup 7.5 software. This course covers general error detection tools and t ... |
|
Register |

|
SECURING CISCO NETWORKS WITH SNORT RULE WRITING BEST PRACTICESSecuring Cisco Networks with Snort Rule Writing Best Practices is a lab-intensive course that introduces students to the open source Snort community and rule-writing best practices. Users focus exclusively on the Snort r ... |
|
Register |

|
IBM QRADAR SIEM FOUNDATIONSIBM QRadar SIEM provides deep visibility into network, user, and application activity. It provides collection, normalization, correlation, and secure storage of events, flows, asset profiles, and vulnerabilities. QRadar ... |
|
Register |

|
CLIENT MANAGEMENT SUITE 8.1 ADMINISTRATIONThe Client Management Suite 8.1 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |
.jpg)
|
EC-COUNCIL CERTIFIED SOC ANALYST (CSA)The Certified SOC Analyst (CSA) program is the first step to joining a security operations center (SOC). It is engineered for current and aspiring Tier I and Tier II SOC analysts to achieve proficiency in performing entr ... |
|
Register |

|
CERTIFIED IN THE GOVERNANCE OF ENTERPRISE ITAs technology has become more and more vital to the achievement of business goals and value delivery, enterprise leaders have realized that enterprise governance must be extended to information technology and information ... |
|
Register |

|
WORKSHOP: WINDOWS SERVER 2019Learn about the new enhanced capabilities of the Windows 2019 starting from server virtualization, storage, software-defined networking, server management and automation, web and application platform, access to informati ... |
|
Register |

|
SYMANTEC CONTROL COMPLIANCE SUITE VULNERABILITY MANAGER 12.0 ADMINISTRATIONThe Symantec Control Compliance Suite Vulnerability Manager (CCS-VM) 12.0 Administration Training is designed for the IT security professional tasked with installation, administering, monitoring and reporting on CCS-VM 1 ... |
|
Register |
|
|
CYBER SEC FIRST RESPONDER™ (CFR) CERTIFICATIONThis course covers network defense and incident response methods, tactics, and procedures are taught in alignment with industry frameworks such as NIST 800-61 r.2 (Computer Security Incident Handling), US-CERT’s NCISP (N ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.5: ADMINISTRATIONThe Symantec Messaging Gateway 10.5: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This three-day, instructor-led, hands-on cl ... |
|
Register |

|
RED HAT SERVER HARDENINGSecure a Red Hat Enterprise Linux system to comply with security policy requirements Red Hat® Server Hardening (RH413) builds on a student's Red Hat Certified Engineer (RHCE®) certification or equivalent experience to t ... |
|
Register |

|
SYMANTEC SSL VISIBILITY 4.3 ADMINISTRATIONThe SSL Visibility 4.3 administration course enables you to plan, implement, configure and managed your SSLV appliance(s). This is a lecture-only course, there will be no hands-on access to an SSLV appliance during the c ... |
|
Register |

|
NSX-T: INSTALL, CONFIGURE, MANAGEThis five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T™ Data Center environment. This course covers key NSX-T Data Center features and functionality offer ... |
|
Register |

|
SECURING CISCO NETWORKS WITH SNORT RULE WRITING BEST PRACTICESSecuring Cisco Networks with Snort Rule Writing Best Practices is a lab-intensive course that introduces students to the open source Snort community and rule-writing best practices. Users focus exclusively on the Snort r ... |
|
Register |

|
EC-COUNCIL NETWORK SECURITY ADMINISTRATORThis course looks at the network security in defensive view. The ENSA program is designed to provide fundamental skills needed to analyze the internal and external security threats against a network, and to develop secur ... |
|
Register |

|
Implementing Cisco Secure MobilityThis course is designed to prepare network security engineers with the knowledge and skills they need to protect data traversing a public or shared infrastructure such as the Internet by implementing and maintaining Cisc ... |
|
Register |
.jpg)
|
FIREWALL 8.1: TROUBLESHOOTING (EDU-330)Successful completion of this three-day, instructor-led course will enhance the participant’s understanding of how to troubleshoot the full line of Palo Alto Networks® next-generation firewalls. Participants will have o ... |
|
Register |

|
IMPLEMENTING FOREFRONT IDENTITY MANAGER 2010This four-day instructor-led course introduces and explains the features and capabilities of Microsoft Forefront Identity Manager 2010 (FIM), and provides an overview of the solution scenarios that FIM addresses. The cou ... |
|
Register |

|
IMPLEMENTING CISCO NETWORK SECURITY V3.0This is a five-day instructor-led course that focuses on the design, implementation and monitoring of a comprehensive security policy, using Cisco IOS security features and technologies. All IOS examples and hands on exp ... |
|
Register |

|
IMPLEMENTING ADVANCED CISCO ASA SECURITY V2.0This course provides up-to-date training on the key features of the Cisco ASA 5500-X Series next-Generation Firewall, including ASAv, ASA IDFW, ASA Fire POWER Service Module, ASA Cloud Web Security and ASA Clustering. Ex ... |
|
Register |

|
SYMANTEC ENDPOINT ENCRYPTION 11.2 INSTALL, CONFIGURE AND DEPLOYThe Symantec Endpoint Encryption 11.2: Install, Configure, and Deploy course is designed for the network, IT security, systems administration, and support professional tasked with maintaining and troubleshooting a Symant ... |
|
Register |

|
IBM DIRECTORY SERVER 6.4 FUNDAMENTALSThis course describes the processes, procedures, and practices necessary to configure and administer IBM Directory Server. During the hand-on exercises, students will perform basic Directory Server configuration, setup r ... |
|
Register |

|
CERTIFIED IN THE GOVERNANCE OF ENTERPRISE ITAs technology has become more and more vital to the achievement of business goals and value delivery, enterprise leaders have realized that enterprise governance must be extended to information technology and information ... |
|
Register |

|
MASTERCLASS: PEN TESTING AND SECURING MOBILE AND WEB APPLICATIONSThe course teaches mobile and web application security concepts, including the techniques on how to attack and how to respond with an appropriate countermeasure implementation. Our course has been developed around profes ... |
|
Register |

|
VMWARE NSX-T DATA CENTER: INSTALL, CONFIGURE, MANAGEThis five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T™ Data Center environment. This course covers key NSX-T Data Center features and functionality offer ... |
|
Register |

|
CONFIGURING JUNIPER NETWORKS FIREWALL/IPSEC VPN PRODUCTSThis course is the first in the Screen OS curriculum. It is a three-day, instructor-led course that focuses on configuration of the Screen OS firewall/virtual private network (VPN) products in a variety of situations, in ... |
|
Register |

|
SECURING THE WEB WITH CISCO WEB SECURITY APPLIANCEThis course has been designed to help learners understand how to install, configure, manage, and troubleshoot a Cisco Web Security Appliance (WSA). Students will learn how to design, configure, administer, monitor, and t ... |
|
Register |

|
MASTERCLASS: RED TEAM - BLUE TEAM OPERATIONSThis is a deep dive course on Red Team – Blue Team Operations: The cyber kill chain Security is a business enabler, and it is only when it is viewed from a business perspective that we can truly make the right decision ... |
|
Register |

|
WORKSHOP: WINDOWS SERVER 2019Learn about the new enhanced capabilities of the Windows 2019 starting from server virtualization, storage, software-defined networking, server management and automation, web and application platform, access to informati ... |
|
Register |
 PREP COURSE.jpg)
|
COMPTIA ADVANCED SECURITY PRACTITIONER (CASP) PREP COURSEYou have experience in the increasingly crucial field of information security, and now you're ready to take that experience to the next level. CompTIA® Advanced Security Practitioner (CASP) (Exam CAS-002) is the course y ... |
|
Register |

|
EC-COUNCIL CERTIFIED SECURITY ANALYST V.10The ECSA program offers a seamless learning progress continuing where the CEH program left off. The new ECSAv10 includes updated curricula and an industry recognized comprehensive step-by step penetration testing method ... |
|
Register |

|
MANAGING ENTERPRISE SECURITY WITH CISCO SECURITY MANAGERThe Managing Enterprise Security with Cisco Security Manager (SSECMGT) course is aimed at providing network security engineers with the knowledge and skills that are needed to configure and deploy Cisco Security Manager. ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS SECURITY PROFESSIONALThe Official (ISC)2® CISSP® CBK® Review Seminar is the most comprehensive, complete review of information systems security concepts and industry best practices, and the only review course endorsed by (ISC)2. Review Semin ... |
|
Register |

|
TREND MICRO DEEP DISCOVERY TRAINING FOR CERTIFIED PROFESSIONALSTrend Micro™ Deep Discovery Training for Certified Professionals is a three-day, instructor-led training course where participants will learn how to deploy and manage a Trend Micro™ Deep Discovery threat protection solut ... |
|
Register |

|
DEV SEC OPS ENGINEERINGA Dev Sec Ops Engineer is an IT Security professional who is skilled at “security as code” with the intent of making security and compliance consumable as a service. A Dev Sec Ops Engineer uses data and security science ... |
|
Register |

|
SYMANTEC ASSET MANAGEMENT SUITE 8.1 ADMINISTRATIONThe Symantec Asset Management Suite 8.1 Administration course is designed for professionals tasked with using Symantec Asset Management Suite (AMS) to manage their software and hardware resources in their organizations. ... |
|
Register |

|
BLUE COAT CERTIFIED SECURITY ANALYTICS ADMINISTRATORThe Blue Coat Certified Security Analytics Administrator (BCSAA) course is intended for IT professionals who want to master the fundamentals of the Blue Coat Security Analytics solution. |
|
Register |

|
CISCO ASA EXPRESS SECURITY 1.5This course has been designed to provide an understanding of Cisco's ASA solution portfolio. Students will learn how to successfully configure various aspects of the Cisco ASA components including Cisco ASA firewall feat ... |
|
Register |

|
SYMANTEC CLOUD SOC ADMINISTRATION R2The Cloud SOC R2 Administration course provides an overview of the Cloud SOC service, covering initial setup, deployment options and service configuration. The courseware introduces each topic with an accompanying workfl ... |
|
Register |

|
Channel Partner Securing Email with Cisco Email Security ApplianceThis course is designed to help learners understand how to install, configure, and manage the Cisco Email Security Appliance in a small to medium-sized business and enterprise installation. Knowledge application and basi ... |
|
Register |

|
SECURING CISCO NETWORKS WITH OPEN SOURCE SNORTSecuring Cisco Networks with Open Source Snort is a lab-intensive course that introduces students to the open source Snort technology as well as rule writing. You will learn how to build and manage a Snort system using o ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.6 ADMINISTRATIONThe Symantec Messaging Gateway 10.6: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This two-day, instructor-led, hand son clas ... |
|
Register |

|
CISSP CERTIFICATION PREP COURSE V1.0Gain core knowledge and experience to successfully implement and manage security programs and prepare for the CISSP certification. This course is the most comprehensive review of information security concepts and industr ... |
|
Register |

|
SYSTEMS SECURITY CERTIFIED PRACTITIONERLooking to move up in the information security field? If you have at least one year of security experience, you qualify for the Systems Security Certified Practitioner (SSCP) certification, which offers junior security p ... |
|
Register |
.png)
|
PALO ALTO ADVANCED FIREWALL TROUBLESHOOTING (311)Advanced Firewall Troubleshooting is the next-level follow-on course to Palo Alto Networks® Essentials 1: Installation, Configuration, and Management (PAN-EDU-201) and Essentials 2: Extended Firewall Manager (PAN-EDU-205 ... |
|
Register |

|
CISCO ASA WITH FIREPOWER SERVICES WORKSHOPThe Cisco Next-Generation Firewall (NGFW) is the industry’s first fully integrated, threat-focused NGFW. It delivers comprehensive, unified policy management of firewall functions, application control, threat prevention, ... |
|
Register |

|
SECURING EMAIL WITH CISCO EMAIL SECURITY APPLIANCEThe Securing Email with Cisco Email Security Appliance (SESA) v3.0 course shows you how to deploy and use Cisco® Email Security Appliance to establish protection for your email systems against phishing, business email co ... |
|
Register |
.jpg)
|
RED HAT IDENTITY MANAGEMENT AND ACTIVE DIRECTORY INTEGRATION WITH EXAM (EX362)This course teaches you skills on the most requested Red Hat Identity Management (IdM) capabilities, including Active Directory trusts, multi-product federation, configuration management with Ansible, integrated certific ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 15.5 ADMINISTRATIONThe Symantec Data Loss Prevention 15.5 Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands‐on labs inc ... |
|
Register |

|
Blue Coat Certified Proxy AdministratorThe Blue Coat Certified Proxy SG Professional (BCCPP) Course is intended for IT professionals who wish to master the advance features of the Blue Coat Proxy SG. |
|
Register |

|
EC-COUNCIL CERTIFIED INCIDENT HANDLERThe EC-Council Certified Incident Handler (ECIH) program is designed to provide the fundamental skills to handle and respond to the computer security incidents in an information system. The course addresses various under ... |
|
Register |

|
CERTIFIED SECURE COMPUTER USER - AWARENESS TRAININGThe purpose of the CSCU training program is to provide individuals with the necessary knowledge and skills to protect their information assets. This class will immerse students into an interactive environment where they ... |
|
Register |

|
SYMANTEC DEPLOYMENT SOLUTION 8.1 ADMINISTRATIONThe Symantec Deployment Solution 8.1: Administration course is designed for the professional tasked with installing, configuring, and managing a Deployment Solution system. This five-day, instructor-led, hands-on course ... |
|
Register |

|
JNCIE-SEC BOOT CAMPThis five-day course is designed to serve as the ultimate preparation for the Juniper Networks Certified Internet Expert—Security (JNCIE-SEC) exam. The course focuses on caveats and tips useful for potential test candida ... |
|
Register |

|
Certified Cloud Security Professional Certification PreparationAs powerful as cloud computing is for the organization, understanding its information security risks and mitigation strategies is critical. Legacy approaches are inadequate, and organizations need competent, experienced ... |
|
Register |
.jpg)
|
PALO ALTO EXTENDED FIREWALL MANAGEMENT (205)Extended Firewall Management is the next-level follow-on course to Palo Alto Networks® Installation, Configuration, and Management (PAN-EDU-201). Extended Firewall Management expands on 201 course topics, while introduci ... |
|
Register |

|
COMPUTER HACKING FORENSICS INVESTIGATORThe CHFI course will give participants the necessary skills to identify an intruder's footprints and to properly gather the necessary evidence to prosecute. Many of today's top tools of the forensic trade will be taught ... |
|
Register |

|
SECURITY+The Security+ Certification Prep Course provides the basic knowledge needed to plan, implement, and maintain information security in a vendor-neutral format. This includes risk management, host and network security, auth ... |
|
Register |
.jpg)
|
LEAD AUDITOR TRAINING (IRCA CERTIFIED)This five-day intensive course enables participants to develop the expertise needed to audit an Information Security Management System (ISMS) and to manage a team of auditors by applying widely recognized audit principle ... |
|
Register |

|
CLIENT MANAGEMENT SUITE 8.1 ADMINISTRATIONThe Client Management Suite 8.1 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |

|
IMPLEMENTING CISCO EDGE NETWORK SECURITY SOLUTIONSThis course has been designed to provide students with the knowledge and skills required to implement and manage security on Cisco ASA firewalls, Cisco Routers with the firewall feature set and Cisco Switches. Students w ... |
|
Register |

|
WEB SECURITY SERVICE 6.10 DIAGNOSTICS AND TROUBLESHOOTINGThe WSS Diagnostics and Troubleshooting course is intended for IT professionals who will be diagnosing and troubleshooting the Symantec Web Security Service (WSS). |
|
Register |

|
SYMANTEC CONTROL COMPLIANCE SUITE VULNERABILITY MANAGER 12.0 ADMINISTRATIONThe Symantec Control Compliance Suite Vulnerability Manager (CCS-VM) 12.0 Administration Training is designed for the IT security professional tasked with installation, administering, monitoring and reporting on CCS-VM 1 ... |
|
Register |

|
IBM SECURITY IDENTITY MANAGER FOUNDATIONSThis is an instructor-led course that introduces students to the foundational skills required to install, configure, and administer IBM Security Identity Manager,. IBM Security Identity Manager can be deployed using the ... |
|
Register |

|
CompTIA Pentest +As organizations scramble to protect themselves and their customers against privacy or security breaches, the ability to conduct penetration testing is an emerging skill set that is becoming ever more valuable to the org ... |
|
Register |

|
Protecting Against Malware Threats with Cisco AMP for EndpointsThis lab-intensive course introduces students to the powerful features of Cisco AMP for Endpoints software. A number of step by step attack scenarios will provide an understanding of the operational uses of the product. ... |
|
Register |

|
EC-COUNCIL CERTIFIED ENCRYPTION SPECIALISTThe EC-Council Certified Encryption Specialist (ECES) program introduces professionals and students to the field of cryptography. The participants will learn the foundations of modern symmetric and key cryptography inclu ... |
|
Register |

|
Certified Threat Intelligence AnalystCertified Threat Intelligence Analyst (C|TIA) is a training and credentialing program designed and developed in collaboration with cybersecurity and threat intelligence experts across the globe to help organizations iden ... |
|
Register |

|
CERTIFIED INFORMATION SECURITY MANAGERFive years of experience with audit, IT systems, and security of information systems; systems administration experience; familiarity with TCP/IP; and an understanding of UNIX, Linux, and Windows. This advanced course als ... |
|
Register |

|
SECURING CISCO NETWORKS WITH SOURCE FIRE INTRUSION PREVENTION SYSTEMThe Securing Networks with Cisco Firepower Next-Generation IPS course shows you how to deploy and use Cisco Firepower Next-Generation Intrusion Prevention System (NGIPS). This hands-on course gives you the knowledge and ... |
|
Register |

|
UNDERSTANDING CISCO CYBER SECURITY FUNDAMENTALSThe Understanding Cisco Cyber security Fundamentals (SECFND) v1.0 course provides you with an understanding of network infrastructure devices, operations and vulnerabilities of the TCP/IP protocol suite, basic informatio ... |
|
Register |

|
SYMANTEC NETBACKUP 7.5: MAINTAIN AND TROUBLESHOOTThe three day Symantec Net Backup Maintain and Troubleshoot course provides the IT professional with instruction on troubleshooting Symantec NetBackup 7.5 software. This course covers general error detection tools and t ... |
|
Register |

|
SYMANTEC DATA CENTER SECURITY SERVER ADVANCED 6.7 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec Data Center Server Advanced 6.7 Diagnostics and Troubleshooting course is designed for the IT security management professional tasked with troubleshooting Data Center Security Server Advanced (SDCSSA). Stud ... |
|
Register |

|
CERTIFIED CHIEF INFORMATION SECURITY OFFICEREC-Council’s CCISO Program has certified leading information security professionals around the world. A core group of high-level information security executives, the CCISO Advisory Board, contributed by forming the found ... |
|
Register |

|
SYMANTEC WEB SECURITY SERVICE CORE ADMINISTRATION R1The Web Security Service Core Administration course is intended for IT professionals who will be installing, configuring or administering the Symantec Web Security Service (WSS). |
|
Register |

|
ETHICAL HACKING AND COUNTERMEASURES V.10The Certified Ethical Hacker (C|EH v10) program is a trusted and respected ethical hacking training Program that any information security professional will need. Since its inception in 2003, the Certified Ethical Hacker ... |
|
Register |
.jpg)
|
PANORAMA 8.1: MANAGING FIREWALLS AT SCALE (EDU-220)This course will help students to gain in-depth knowledge about how to configure and manage their Palo Alto Networks® Panorama TM management server. Upon completion of this course, administrators should be familiar with ... |
|
Register |

|
SYMANTEC PROXY SG V6.6: ADVANCED ADMINISTRATIONThe Proxy SG v6.6 Advanced Administration course is intended for IT professionals who wish to learn to master the advanced features of Proxy SG. |
|
Register |

|
EC-COUNCIL CERTIFIED NETWORK DEFENDERCertified Network Defender (CND) is a vendor-neutral, hands-on, instructor-led comprehensive network security certification training program. It is a skills-based, lab intensive program based on a job-task analysis and c ... |
|
Register |

|
EC - COUNCIL CERTIFIED SECURE PROGRAMMERSoftware defects, bugs, and flaws in the logic of the program are consistently the cause for software vulnerabilities. Analysis by software security professionals has proven that most vulnerabilities are due to errors i ... |
|
Register |
|
COMPTIA CSA+ CYBERSECURITY ANALYSTThe CompTIA CSA+ certification is a vendor-neutral credential. The CompTIA CSA+ exam (Exam CS0-001) is an internationally targeted validation of intermediate-level security skills and knowledge. The course has a technica ... |
|
Register |

|
IMPLEMENTING CISCO UNIFIED COMMUNICATIONS SECURITYThe Implementing Cisco Unified Communications Security (UCSEC) course is designed to provide students with the necessary knowledge and skills to implement security features in a Cisco Unified Communications environment. ... |
|
Register |

|
SYMANTEC NET BACKUP 7.6.X: ADMINISTRATIONThis Symantec Net Backup 7.6.x: Administration course provides the IT professional with instruction on the functionality of Symantec NetBackup 7.6.1 software. This course covers the general principles of using NetBackup ... |
|
Register |

|
Implementing Cisco Identity Services Engine for Wireless EngineersThis course has been designed to enable wireless engineers understand the concepts, architecture, and use cases of the Cisco Identity Services Engine Solution. This course provides students with the knowledge and skills ... |
|
Register |

|
CERTIFIED SECURE COMPUTER USER - AWARENESS TRAININGThe purpose of the CSCU training program is to provide individuals with the necessary knowledge and skills to protect their information assets. This class will immerse students into an interactive environment where they ... |
|
Register |

|
IBM GUARDIUM FOUNDATIONSAre you getting ready to administer database security policies? Learn how to configure Guardium to discover, classify, analyze, protect, and control access to sensitive data. You learn to perform vulnerability assessment ... |
|
Register |

|
CYBERSECURITY FOUNDATIONSWhen you consider just a few of the consequences of a security breach - your proprietary information completely accessible, hefty fines for security lapses, news headlines about your company's security breach, it becomes ... |
|
Register |

|
SYMANTEC IT MANAGEMENT SUITE 8.1 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec IT Management Suite 8.1 Diagnostics and Troubleshooting course is designed for professionals tasked with maintaining and utilizing a Symantec IT Management Suite (ITMS) implementation in their organizations. ... |
|
Register |

|
MASTER CLASS ISO 27001 IMPLEMENTATIONThis five-day intensive course enables the participants to develop the expertise to support an organization in implementing and managing an Information Security Management System (ISMS) as specified in ISO/IEC 27001:2013 ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS AUDITORCISA® is a trademark of the Information Systems Audit and Control Association® (ISACA®) More than 60,000 security professionals hold CISA certification, which was awarded the "Best Professional Certification" for 2009 b ... |
|
Register |

|
SYMANTEC SSL VISIBILITY 4.3 ADMINISTRATIONThe SSL Visibility 4.3 administration course enables you to plan, implement, configure and managed your SSLV appliance(s). This is a lecture-only course, there will be no hands-on access to an SSLV appliance during the c ... |
|
Register |

|
IBM IDENTITY GOVERNANCE AND INTELLIGENCE FOUNDATIONSIBM Identity Governance and Intelligence is an advanced identity governance system. This course provides the foundational skills necessary to operate, administer, and accomplish the major business functions and analyses ... |
|
Register |
.jpg)
|
CISCO CCNA SECURITY BOOT CAMP (ACCELERATED)In this course, you will learn how to install, operate, configure, and verify a basic IPv4 and IPv6 network, including configuring a LAN switch, configuring an IP router, managing network devices. You will also learn abo ... |
|
Register |

|
IBM SECURITY QRADAR SIEM ADVANCED TOPICSThis is an advanced course for the QRadar Analyst and Administrator and is a follow-on to BQ103G. This course uses the IBM QRadar SIEM 7.3 platform for lab exercises. |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 14.6 ADMINISTRATIONThe Symantec Data Loss Prevention 14.X: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands-on labs i ... |
|
Register |

|
SYMANTEC SECURITY ANALYTICS 7.2.X PROFESSIONALThe Symantec Security Analytics Professional course is designed for participants who want to learn how to use the Symantec Security Analytics platform to perform virtually any type of network-based monitoring and forensi ... |
|
Register |

|
CONFIGURING AND DEPLOYING A PRIVATE CLOUDThis course equips students with the skills they require to configure and deploy a cloud using Microsoft System Center 2012 R2. Using hands-on labs, students learn the following: - Produce a high-level design that acc ... |
|
Register |

|
IMPLEMENTING CISCO CYBERSECURITY OPERATIONSThis is the second course in Cisco's CCNA Cyber Ops Curriculum and is designed to provide students with an understanding of how a Security Operations Center (SOC) functions and the knowledge required in this environment. ... |
|
Register |
 CERTIFICATION44.jpg)
|
CERTIFIED INTERNET OF THINGS PRACTITIONER (CIOTP) CERTIFICATIONThe Internet of Things (IoT) promises a wide range of benefits for industry, energy and utility companies, municipalities, healthcare, and consumers. Data can be collected in extraordinary volume and detail regarding alm ... |
|
Register |

|
WEB SECURITY SERVICE 6.10 DIAGNOSTICS AND TROUBLESHOOTINGThe WSS Diagnostics and Troubleshooting course is intended for IT professionals who will be diagnosing and troubleshooting the Symantec Web Security Service (WSS). |
|
Register |

|
CYBER SEC FIRST RESPONDER: THREAT DETECTION AND RESPONSEThis course covers the duties of those who are responsible for monitoring and detecting security incidents in information systems and networks, and for executing a proper response to such incidents. Depending on the size ... |
|
Register |

|
VMWARE NSX-T DATA CENTER: INSTALL, CONFIGURE, MANAGEThis five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T™ Data Center environment. This course covers key NSX-T Data Center features and functionality offer ... |
|
Register |

|
TREND MICRO DEEP DISCOVERY TRAINING FOR CERTIFIED PROFESSIONALSTrend Micro™ Deep Discovery Training for Certified Professionals is a three-day, instructor-led training course where participants will learn how to deploy and manage a Trend Micro™ Deep Discovery threat protection solut ... |
|
Register |

|
SYMANTEC PROXY SG V6.6: BASIC ADMINISTRATIONThe Proxy SG 6.6 Basic Administration course is an introduction to deployment options and management of the individual key features offered using the Proxy SG 6.6 solution. This an introductory course and is designed for ... |
|
Register |
.jpg)
|
EC-COUNCIL CERTIFIED SOC ANALYST (CSA)The Certified SOC Analyst (CSA) program is the first step to joining a security operations center (SOC). It is engineered for current and aspiring Tier I and Tier II SOC analysts to achieve proficiency in performing entr ... |
|
Register |

|
IMPLEMENTING CISCO THREAT CONTROL SYSTEMSImplementing Cisco Threat Control Solutions is designed to provide security engineers with the knowledge and hands-on experience required to deploy Cisco’s Email Security (ESA); Web Security (CWS, WSA); Advanced Malware ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 15.0 ADMINISTRATIONThe Symantec Data Loss Prevention 15.0 Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands-on labs inc ... |
|
Register |

|
PERFORMANCE TUNING AND OPTIMIZING SQL DATABASESThis four-day instructor-led course provides students who manage and maintain SQL Server databases with the knowledge and skills to performance tune and optimize their databases. |
|
Register |

|
TREND MICRO APEX ONE TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro Apex One™. This course details basic architecture, protection functionality, deployment scenarios, and troubleshooting. Through hands-on labs, participants practice c ... |
|
Register |

|
DEPLOYING AND MANAGING WINDOWS 10 USING ENTERPRISE SERVICESThis 5-day course provides administrators with the knowledge and skills needed to deploy and manage Windows 10 desktops, devices, and applications in an enterprise environment. Students learn how to plan and implement Wi ... |
|
Register |

|
MANAGING AND DEFENDING AGAINST CURRENT THREATSThis is a deep dive course on security operations: vulnerability management, anomalies detection, discovery of industry attacks and threats, understanding how compromised system or solution looks like, defining the indic ... |
|
Register |

|
BLUE COAT CERTIFIED SECURITY ANALYTICS PROFESSIONALThe Blue Coat Certified Security Analytics Professional (BCSAP) course designed for participants who want to learn how to use the Blue Coat Security Analytics platform to perform virtually any type of network-based monit ... |
|
Register |

|
RED HAT SECURITY: SECURING CONTAINERS AND OPEN SHIFT WITH EXAMYou will learn and validate your skills in using secure and trusted container images, registries, and source code; managing network and storage isolation; implementing application single sign-on; and configuring appropri ... |
|
Register |

|
CITRIX ENTERPRISE SECURITY SOLUTIONSLearn to secure your Citrix environment in this hands-on course that encompasses the core Citrix technologies, including Citrix Virtual Apps and Desktops, ADC, Endpoint Management, Content Collaboration and Citrix Cloud. ... |
|
Register |

|
SYMANTEC IDENTITY AND AUTHENTICATION SERVICES R1The Symantec Identity and Authentication Services R1 course is designed for the IT security professional needing to develop an understanding of the principles and use cases behind the Symantec VIP Service and VIP Access ... |
|
Register |

|
BLUE COAT PACKET SHAPER PROFESSIONALBlue Coat Certified Packet Shaper Administrator (BCPSA) certification or waiver exam; student should have practical experience with the Packet Shaper appliance in the field with a solid understanding of networking and ge ... |
|
Register |

|
JUNOS SPACE-SECURITY DIRECTORThis two-day course is designed to provide students with the knowledge required to manage the Junos Space Security Director application and manage devices with that application. Students will gain in-depth knowledge of h ... |
|
Register |
.png)
|
FIREWALL 8.1: OPTIMIZING FIREWALL THREAT PREVENTION (EDU-214)Successful completion of this four-day, instructor-led course will enhance the student’s understanding of how to better configure, manage, and monitor PAN-OS® threat prevention features. The student will get hands-on exp ... |
|
Register |

|
SYMANTEC ASSET MANAGEMENT SUITE 8.5 ADMINISTRATIONThe Symantec Asset Management Suite 8.5 Administration course is designed for professionals tasked with using Symantec Asset Management Suite (AMS) to manage their software and hardware resources in their organizations. ... |
|
Register |

|
SYMANTEC SSL VISIBILITY 5.0 ADMINISTRATIONThe SSL Visibility 5.0 Administration course enables you to plan, implement, configure and managed your SSLV virtual appliance. This course includes both lecture and hands-on labs that access the SSLV virtual appliance. ... |
|
Register |

|
DEEP SECURITY TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro™ Deep Security. This course provides information about the basic architecture, deployment scenarios, installation processes, policy configuration and administration o ... |
|
Register |

|
IBM ACCESS MANAGER PLATFORM FOUNDATIONSIBM Access Manager is a highly scalable and configurable access management solution. It simplifies and secures your user experience with single sign-on across applications and protects critical assets using strong multi- ... |
|
Register |

|
SYMANTEC SECURITY ANALYTICS 7.2.X PROFESSIONALThe Symantec Security Analytics Professional course is designed for participants who want to learn how to use the Symantec Security Analytics platform to perform virtually any type of network-based monitoring and forensi ... |
|
Register |

|
JUNOS INTRUSION PREVENTION SYSTEM FUNCTIONALITYThe Junos Intrusion prevention System Functionality (JIPS) course is designed to provide an introduction to the Intrusion Prevention System (IPS) feature set available on the Juniper Networks SRX Series Services Gateway. ... |
|
Register |

|
CERTIFIED IN RISK AND INFORMATION SYSTEMS CONTROLThe CRISC Review Manual and CRISC Review, Questions, Answers and Explanation Manual will be provided to delegates booked on the course. |
|
Register |

|
EC-COUNCIL CERTIFIED SECURITY ANALYST V.10The ECSA program offers a seamless learning progress continuing where the CEH program left off. The new ECSAv10 includes updated curricula and an industry recognized comprehensive step-by step penetration testing method ... |
|
Register |
.jpg)
|
RED HAT SECURITY: LINUX IN PHYSICAL, VIRTUAL, AND CLOUD WITH EXAM (EX415)Maintaining security of computing systems is a process of managing risk through the implementation of processes and standards backed by technologies and tools. In this course, you will learn about resources that can be u ... |
|
Register |
.jpg)
|
FIREWALL 8.1: TROUBLESHOOTING (EDU-330)Successful completion of this three-day, instructor-led course will enhance the participant’s understanding of how to troubleshoot the full line of Palo Alto Networks® next-generation firewalls. Participants will have o ... |
|
Register |

|
SECURING CISCO NETWORKS WITH OPEN SOURCE SNORTSecuring Cisco Networks with Open Source Snort is a lab-intensive course that introduces students to the open source Snort technology as well as rule writing. You will learn how to build and manage a Snort system using o ... |
|
Register |

|
ETHICAL HACKING AND COUNTERMEASURES V.10The Certified Ethical Hacker (C|EH v10) program is a trusted and respected ethical hacking training Program that any information security professional will need. Since its inception in 2003, the Certified Ethical Hacker ... |
|
Register |

|
SYMANTEC CONTROL COMPLIANCE SUITE 12.0 ADMINISTRATIONThe Control Compliance Suite 12.0 Administration course is designed for professionals who are tasked with ensuring the security of their computing enterprise and compliance with both external and internal mandates. This ... |
|
Register |

|
CYBERSECURITY FOUNDATIONSWhen you consider just a few of the consequences of a security breach - your proprietary information completely accessible, hefty fines for security lapses, news headlines about your company's security breach, it becomes ... |
|
Register |

|
IBM QRADAR SIEM FOUNDATIONSIBM QRadar SIEM provides deep visibility into network, user, and application activity. It provides collection, normalization, correlation, and secure storage of events, flows, asset profiles, and vulnerabilities. QRadar ... |
|
Register |

|
Implementing Forefront Unified Access Gateway 2010This three-day instructor-led course prepares you to design and deploy remote access solutions using Microsoft Forefront Unified Access Gateway 2010 (UAG). Forefront UAG provides organizations with unparalleled flexibili ... |
|
Register |
 PREP COURSE.jpg)
|
COMPTIA ADVANCED SECURITY PRACTITIONER (CASP) PREP COURSEYou have experience in the increasingly crucial field of information security, and now you're ready to take that experience to the next level. CompTIA® Advanced Security Practitioner (CASP) (Exam CAS-002) is the course y ... |
|
Register |
.png)
|
PALO ALTO ADVANCED FIREWALL TROUBLESHOOTING (311)Advanced Firewall Troubleshooting is the next-level follow-on course to Palo Alto Networks® Essentials 1: Installation, Configuration, and Management (PAN-EDU-201) and Essentials 2: Extended Firewall Manager (PAN-EDU-205 ... |
|
Register |

|
SYMANTEC WEB SECURITY SERVICE CORE ADMINISTRATION R1The Web Security Service Core Administration course is intended for IT professionals who will be installing, configuring or administering the Symantec Web Security Service (WSS). |
|
Register |

|
MASTERCLASS: PEN TESTING AND SECURING MOBILE AND WEB APPLICATIONSThe course teaches mobile and web application security concepts, including the techniques on how to attack and how to respond with an appropriate countermeasure implementation. Our course has been developed around profes ... |
|
Register |

|
SECURING THE WEB WITH CISCO WEB SECURITY APPLIANCEThis course has been designed to help learners understand how to install, configure, manage, and troubleshoot a Cisco Web Security Appliance (WSA). Students will learn how to design, configure, administer, monitor, and t ... |
|
Register |

|
SYMANTEC ENDPOINT ENCRYPTION 11.2 INSTALL, CONFIGURE AND DEPLOYThe Symantec Endpoint Encryption 11.2: Install, Configure, and Deploy course is designed for the network, IT security, systems administration, and support professional tasked with maintaining and troubleshooting a Symant ... |
|
Register |

|
NETWORK AND SECURITY MANAGER FUNDAMENTALSThis two-day course discusses the basic operations of Network and Security Manager. Key topics include server and domain administration, device configuration, template creation and management, policy creation and managem ... |
|
Register |

|
IMPLEMENTING AND CONFIGURING CISCO IDENTITY SERVICES ENGINEThe Implementing and Configuring Cisco Identity Services Engine course shows you how to deploy and use Cisco Identity Services Engine (ISE) v2.4, an identity and access control policy platform that simplifies the deliver ... |
|
Register |

|
SYSTEMS SECURITY CERTIFIED PRACTITIONERLooking to move up in the information security field? If you have at least one year of security experience, you qualify for the Systems Security Certified Practitioner (SSCP) certification, which offers junior security p ... |
|
Register |

|
Certified Cloud Security Professional Certification PreparationAs powerful as cloud computing is for the organization, understanding its information security risks and mitigation strategies is critical. Legacy approaches are inadequate, and organizations need competent, experienced ... |
|
Register |

|
IBM SECURITY IDENTITY MANAGER FOUNDATIONSThis is an instructor-led course that introduces students to the foundational skills required to install, configure, and administer IBM Security Identity Manager,. IBM Security Identity Manager can be deployed using the ... |
|
Register |

|
RHS333-BUNDLE: RED HAT ENTERPRISE SECURITY: NETWORK SERVICES + EX333Red Hat® Enterprise Security: Network Services with Exam is an intensive course that provides 4 days of instruction and labs that show students how to use the latest technologies to secure services. This class advances b ... |
|
Register |

|
JUNOS SECURITYThis five-day course covers the configuration, operation, and implementation of SRX Series Services Gateways in a typical network environment. Key topics within this course include: security zones, security policies, Net ... |
|
Register |
.jpg)
|
PALO ALTO EXTENDED FIREWALL MANAGEMENT (205)Extended Firewall Management is the next-level follow-on course to Palo Alto Networks® Installation, Configuration, and Management (PAN-EDU-201). Extended Firewall Management expands on 201 course topics, while introduci ... |
|
Register |

|
SYMANTEC SSL VISIBILITY 5.0 ADMINISTRATIONThe SSL Visibility 5.0 Administration course enables you to plan, implement, configure and managed your SSLV virtual appliance. This course includes both lecture and hands-on labs that access the SSLV virtual appliance. ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS AUDITORCISA® is a trademark of the Information Systems Audit and Control Association® (ISACA®) More than 60,000 security professionals hold CISA certification, which was awarded the "Best Professional Certification" for 2009 b ... |
|
Register |
 CERTIFICATION.png)
|
CYBER SECURE CODER (CSC) CERTIFICATIONThe stakes for software security are very high, and yet many development teams deal with software security only after the code has been developed and the software is being prepared for delivery. As with any aspect of sof ... |
|
Register |

|
CompTIA Security+CompTIA Security+ (SY0-601) is a course designed to teach IT professionals the fundamentals of information security. The course covers everything from basic security concepts to advanced topics like identity management a ... |
|
Register |

|
CompTIA Security+CompTIA Security+ (SY0-601) is a course designed to teach IT professionals the fundamentals of information security. The course covers everything from basic security concepts to advanced topics like identity management a ... |
|
Register |
Saudi Arabia , Dammam |
|||
|---|---|---|---|

|
MASTERCLASS: RED TEAM - BLUE TEAM OPERATIONSThis is a deep dive course on Red Team – Blue Team Operations: The cyber kill chain Security is a business enabler, and it is only when it is viewed from a business perspective that we can truly make the right decision ... |
|
Register |

|
IMPLEMENTING ADVANCED CISCO ASA SECURITY V2.0This course provides up-to-date training on the key features of the Cisco ASA 5500-X Series next-Generation Firewall, including ASAv, ASA IDFW, ASA Fire POWER Service Module, ASA Cloud Web Security and ASA Clustering. Ex ... |
|
Register |

|
CISCO ASA EXPRESS SECURITY 1.5This course has been designed to provide an understanding of Cisco's ASA solution portfolio. Students will learn how to successfully configure various aspects of the Cisco ASA components including Cisco ASA firewall feat ... |
|
Register |

|
SECURING CISCO NETWORKS WITH SOURCE FIRE INTRUSION PREVENTION SYSTEMThe Securing Networks with Cisco Firepower Next-Generation IPS course shows you how to deploy and use Cisco Firepower Next-Generation Intrusion Prevention System (NGIPS). This hands-on course gives you the knowledge and ... |
|
Register |

|
Channel Partner Securing Email with Cisco Email Security ApplianceThis course is designed to help learners understand how to install, configure, and manage the Cisco Email Security Appliance in a small to medium-sized business and enterprise installation. Knowledge application and basi ... |
|
Register |
.jpg)
|
PALO ALTO EXTENDED FIREWALL MANAGEMENT (205)Extended Firewall Management is the next-level follow-on course to Palo Alto Networks® Installation, Configuration, and Management (PAN-EDU-201). Extended Firewall Management expands on 201 course topics, while introduci ... |
|
Register |

|
CISCO ASA WITH FIREPOWER SERVICES WORKSHOPThe Cisco Next-Generation Firewall (NGFW) is the industry’s first fully integrated, threat-focused NGFW. It delivers comprehensive, unified policy management of firewall functions, application control, threat prevention, ... |
|
Register |

|
SYMANTEC CLOUD SOC ADMINISTRATION R2The Cloud SOC R2 Administration course provides an overview of the Cloud SOC service, covering initial setup, deployment options and service configuration. The courseware introduces each topic with an accompanying workfl ... |
|
Register |

|
ETHICAL HACKING AND COUNTERMEASURES V.10The Certified Ethical Hacker (C|EH v10) program is a trusted and respected ethical hacking training Program that any information security professional will need. Since its inception in 2003, the Certified Ethical Hacker ... |
|
Register |

|
RED HAT SECURITY: SECURING CONTAINERS AND OPEN SHIFT WITH EXAMYou will learn and validate your skills in using secure and trusted container images, registries, and source code; managing network and storage isolation; implementing application single sign-on; and configuring appropri ... |
|
Register |

|
Implementing Forefront Unified Access Gateway 2010This three-day instructor-led course prepares you to design and deploy remote access solutions using Microsoft Forefront Unified Access Gateway 2010 (UAG). Forefront UAG provides organizations with unparalleled flexibili ... |
|
Register |
 PREP COURSE.jpg)
|
COMPTIA ADVANCED SECURITY PRACTITIONER (CASP) PREP COURSEYou have experience in the increasingly crucial field of information security, and now you're ready to take that experience to the next level. CompTIA® Advanced Security Practitioner (CASP) (Exam CAS-002) is the course y ... |
|
Register |

|
EC-COUNCIL NETWORK SECURITY ADMINISTRATORThis course looks at the network security in defensive view. The ENSA program is designed to provide fundamental skills needed to analyze the internal and external security threats against a network, and to develop secur ... |
|
Register |

|
CYBER SEC FIRST RESPONDER: THREAT DETECTION AND RESPONSEThis course covers the duties of those who are responsible for monitoring and detecting security incidents in information systems and networks, and for executing a proper response to such incidents. Depending on the size ... |
|
Register |

|
Implementing Cisco Identity Services Engine for Wireless EngineersThis course has been designed to enable wireless engineers understand the concepts, architecture, and use cases of the Cisco Identity Services Engine Solution. This course provides students with the knowledge and skills ... |
|
Register |

|
Blue Coat Certified Proxy AdministratorThe Blue Coat Certified Proxy SG Professional (BCCPP) Course is intended for IT professionals who wish to master the advance features of the Blue Coat Proxy SG. |
|
Register |

|
IBM SECURITY QRADAR SIEM ADVANCED TOPICSThis is an advanced course for the QRadar Analyst and Administrator and is a follow-on to BQ103G. This course uses the IBM QRadar SIEM 7.3 platform for lab exercises. |
|
Register |

|
DEV SEC OPS ENGINEERINGA Dev Sec Ops Engineer is an IT Security professional who is skilled at “security as code” with the intent of making security and compliance consumable as a service. A Dev Sec Ops Engineer uses data and security science ... |
|
Register |

|
SYMANTEC NET BACKUP 7.6.X: ADMINISTRATIONThis Symantec Net Backup 7.6.x: Administration course provides the IT professional with instruction on the functionality of Symantec NetBackup 7.6.1 software. This course covers the general principles of using NetBackup ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS AUDITORCISA® is a trademark of the Information Systems Audit and Control Association® (ISACA®) More than 60,000 security professionals hold CISA certification, which was awarded the "Best Professional Certification" for 2009 b ... |
|
Register |

|
BLUE COAT CERTIFIED SECURITY ANALYTICS PROFESSIONALThe Blue Coat Certified Security Analytics Professional (BCSAP) course designed for participants who want to learn how to use the Blue Coat Security Analytics platform to perform virtually any type of network-based monit ... |
|
Register |
.jpg)
|
RED HAT SECURITY: LINUX IN PHYSICAL, VIRTUAL, AND CLOUD WITH EXAM (EX415)Maintaining security of computing systems is a process of managing risk through the implementation of processes and standards backed by technologies and tools. In this course, you will learn about resources that can be u ... |
|
Register |

|
Implementing Cisco Secure MobilityThis course is designed to prepare network security engineers with the knowledge and skills they need to protect data traversing a public or shared infrastructure such as the Internet by implementing and maintaining Cisc ... |
|
Register |

|
EC-COUNCIL CERTIFIED INCIDENT HANDLERThe EC-Council Certified Incident Handler (ECIH) program is designed to provide the fundamental skills to handle and respond to the computer security incidents in an information system. The course addresses various under ... |
|
Register |
.png)
|
PALO ALTO ADVANCED FIREWALL TROUBLESHOOTING (311)Advanced Firewall Troubleshooting is the next-level follow-on course to Palo Alto Networks® Essentials 1: Installation, Configuration, and Management (PAN-EDU-201) and Essentials 2: Extended Firewall Manager (PAN-EDU-205 ... |
|
Register |

|
CERTIFIED SECURE COMPUTER USER - AWARENESS TRAININGThe purpose of the CSCU training program is to provide individuals with the necessary knowledge and skills to protect their information assets. This class will immerse students into an interactive environment where they ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 14.6 ADMINISTRATIONThe Symantec Data Loss Prevention 14.X: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands-on labs i ... |
|
Register |

|
MANAGING AND DEFENDING AGAINST CURRENT THREATSThis is a deep dive course on security operations: vulnerability management, anomalies detection, discovery of industry attacks and threats, understanding how compromised system or solution looks like, defining the indic ... |
|
Register |

|
SYMANTEC IDENTITY AND AUTHENTICATION SERVICES R1The Symantec Identity and Authentication Services R1 course is designed for the IT security professional needing to develop an understanding of the principles and use cases behind the Symantec VIP Service and VIP Access ... |
|
Register |

|
JUNOS SECURITYThis five-day course covers the configuration, operation, and implementation of SRX Series Services Gateways in a typical network environment. Key topics within this course include: security zones, security policies, Net ... |
|
Register |

|
IMPLEMENTING CISCO CYBERSECURITY OPERATIONSThis is the second course in Cisco's CCNA Cyber Ops Curriculum and is designed to provide students with an understanding of how a Security Operations Center (SOC) functions and the knowledge required in this environment. ... |
|
Register |

|
SYMANTEC CONTROL COMPLIANCE SUITE 12.0 ADMINISTRATIONThe Control Compliance Suite 12.0 Administration course is designed for professionals who are tasked with ensuring the security of their computing enterprise and compliance with both external and internal mandates. This ... |
|
Register |

|
CITRIX ENTERPRISE SECURITY SOLUTIONSLearn to secure your Citrix environment in this hands-on course that encompasses the core Citrix technologies, including Citrix Virtual Apps and Desktops, ADC, Endpoint Management, Content Collaboration and Citrix Cloud. ... |
|
Register |

|
RHS333-BUNDLE: RED HAT ENTERPRISE SECURITY: NETWORK SERVICES + EX333Red Hat® Enterprise Security: Network Services with Exam is an intensive course that provides 4 days of instruction and labs that show students how to use the latest technologies to secure services. This class advances b ... |
|
Register |

|
PERFORMANCE TUNING AND OPTIMIZING SQL DATABASESThis four-day instructor-led course provides students who manage and maintain SQL Server databases with the knowledge and skills to performance tune and optimize their databases. |
|
Register |

|
RED HAT SECURITY: SECURING CONTAINERS AND OPEN SHIFT WITH EXAMYou will learn and validate your skills in using secure and trusted container images, registries, and source code; managing network and storage isolation; implementing application single sign-on; and configuring appropri ... |
|
Register |
 CERTIFICATION.png)
|
CYBER SECURE CODER (CSC) CERTIFICATIONThe stakes for software security are very high, and yet many development teams deal with software security only after the code has been developed and the software is being prepared for delivery. As with any aspect of sof ... |
|
Register |

|
Implementing Forefront Unified Access Gateway 2010This three-day instructor-led course prepares you to design and deploy remote access solutions using Microsoft Forefront Unified Access Gateway 2010 (UAG). Forefront UAG provides organizations with unparalleled flexibili ... |
|
Register |

|
SECURITY+The Security+ Certification Prep Course provides the basic knowledge needed to plan, implement, and maintain information security in a vendor-neutral format. This includes risk management, host and network security, auth ... |
|
Register |

|
BLUE COAT PACKET SHAPER PROFESSIONALBlue Coat Certified Packet Shaper Administrator (BCPSA) certification or waiver exam; student should have practical experience with the Packet Shaper appliance in the field with a solid understanding of networking and ge ... |
|
Register |

|
BLUE COAT CERTIFIED SECURITY ANALYTICS ADMINISTRATORThe Blue Coat Certified Security Analytics Administrator (BCSAA) course is intended for IT professionals who want to master the fundamentals of the Blue Coat Security Analytics solution. |
|
Register |

|
SECURING CISCO NETWORKS WITH SNORT RULE WRITING BEST PRACTICESSecuring Cisco Networks with Snort Rule Writing Best Practices is a lab-intensive course that introduces students to the open source Snort community and rule-writing best practices. Users focus exclusively on the Snort r ... |
|
Register |

|
BLUE COAT CERTIFIED PROXY PROFESSIONALIn the Blue Coat Certified Proxy Professional (BCCPP) course, you will learn to configure your Blue Coat Proxy appliance for high availability and multi-site deployments, advance policy features, web content control, P2P ... |
|
Register |

|
NSX-T: INSTALL, CONFIGURE, MANAGEThis five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T™ Data Center environment. This course covers key NSX-T Data Center features and functionality offer ... |
|
Register |

|
IMPLEMENTING CISCO NETWORK SECURITY V3.0This is a five-day instructor-led course that focuses on the design, implementation and monitoring of a comprehensive security policy, using Cisco IOS security features and technologies. All IOS examples and hands on exp ... |
|
Register |

|
COMPTIA CSA+ CYBERSECURITY ANALYSTThe CompTIA CSA+ certification is a vendor-neutral credential. The CompTIA CSA+ exam (Exam CS0-001) is an internationally targeted validation of intermediate-level security skills and knowledge. The course has a technica ... |
|
Register |

|
IBM GUARDIUM FOUNDATIONSAre you getting ready to administer database security policies? Learn how to configure Guardium to discover, classify, analyze, protect, and control access to sensitive data. You learn to perform vulnerability assessment ... |
|
Register |
.jpg)
|
RED HAT IDENTITY MANAGEMENT AND ACTIVE DIRECTORY INTEGRATION WITH EXAM (EX362)This course teaches you skills on the most requested Red Hat Identity Management (IdM) capabilities, including Active Directory trusts, multi-product federation, configuration management with Ansible, integrated certific ... |
|
Register |

|
ETHICAL HACKING AND COUNTERMEASURES V.10The Certified Ethical Hacker (C|EH v10) program is a trusted and respected ethical hacking training Program that any information security professional will need. Since its inception in 2003, the Certified Ethical Hacker ... |
|
Register |

|
SYMANTEC ASSET MANAGEMENT SUITE 8.1 ADMINISTRATIONThe Symantec Asset Management Suite 8.1 Administration course is designed for professionals tasked with using Symantec Asset Management Suite (AMS) to manage their software and hardware resources in their organizations. ... |
|
Register |

|
COMPUTER HACKING FORENSICS INVESTIGATORThe CHFI course will give participants the necessary skills to identify an intruder's footprints and to properly gather the necessary evidence to prosecute. Many of today's top tools of the forensic trade will be taught ... |
|
Register |

|
SYMANTEC DEPLOYMENT SOLUTION 8.1 ADMINISTRATIONThe Symantec Deployment Solution 8.1: Administration course is designed for the professional tasked with installing, configuring, and managing a Deployment Solution system. This five-day, instructor-led, hands-on course ... |
|
Register |

|
CISCO ASA WITH FIREPOWER SERVICES WORKSHOPThe Cisco Next-Generation Firewall (NGFW) is the industry’s first fully integrated, threat-focused NGFW. It delivers comprehensive, unified policy management of firewall functions, application control, threat prevention, ... |
|
Register |
.jpg)
|
PALO ALTO NETWORKS® TRAPS™ ADVANCED ENDPOINT PROTECTION (PAN-EDU-281)This instructor-led course teaches strategies in defense against advanced threats. Successful completion of this course enables administrators to better understand the threat landscape. Students will learn the use of Pal ... |
|
Register |

|
IMPLEMENTING FOREFRONT IDENTITY MANAGER 2010This four-day instructor-led course introduces and explains the features and capabilities of Microsoft Forefront Identity Manager 2010 (FIM), and provides an overview of the solution scenarios that FIM addresses. The cou ... |
|
Register |

|
IBM ACCESS MANAGER PLATFORM FOUNDATIONSIBM Access Manager is a highly scalable and configurable access management solution. It simplifies and secures your user experience with single sign-on across applications and protects critical assets using strong multi- ... |
|
Register |
Egypt , Cairo |
|||
|---|---|---|---|

|
TREND MICRO APEX ONE TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro Apex One™. This course details basic architecture, protection functionality, deployment scenarios, and troubleshooting. Through hands-on labs, participants practice c ... |
|
Register |
.jpg)
|
PALO ALTO NETWORKS® TRAPS™ ADVANCED ENDPOINT PROTECTION (PAN-EDU-281)This instructor-led course teaches strategies in defense against advanced threats. Successful completion of this course enables administrators to better understand the threat landscape. Students will learn the use of Pal ... |
|
Register |

|
CERTIFIED IN RISK AND INFORMATION SYSTEMS CONTROLThe CRISC Review Manual and CRISC Review, Questions, Answers and Explanation Manual will be provided to delegates booked on the course. |
|
Register |

|
CONFIGURING JUNIPER NETWORKS FIREWALL/IPSEC VPN PRODUCTSThis course is the first in the Screen OS curriculum. It is a three-day, instructor-led course that focuses on configuration of the Screen OS firewall/virtual private network (VPN) products in a variety of situations, in ... |
|
Register |

|
NETWORK AND SECURITY MANAGER FUNDAMENTALSThis two-day course discusses the basic operations of Network and Security Manager. Key topics include server and domain administration, device configuration, template creation and management, policy creation and managem ... |
|
Register |
 CERTIFICATION.png)
|
CYBER SECURE CODER (CSC) CERTIFICATIONThe stakes for software security are very high, and yet many development teams deal with software security only after the code has been developed and the software is being prepared for delivery. As with any aspect of sof ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.6 ADMINISTRATIONThe Symantec Messaging Gateway 10.6: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This two-day, instructor-led, hand son clas ... |
|
Register |

|
CISSP CERTIFICATION PREP COURSE V1.0Gain core knowledge and experience to successfully implement and manage security programs and prepare for the CISSP certification. This course is the most comprehensive review of information security concepts and industr ... |
|
Register |

|
SECURITY+The Security+ Certification Prep Course provides the basic knowledge needed to plan, implement, and maintain information security in a vendor-neutral format. This includes risk management, host and network security, auth ... |
|
Register |

|
SYMANTEC PROXY SG V6.6: BASIC ADMINISTRATIONThe Proxy SG 6.6 Basic Administration course is an introduction to deployment options and management of the individual key features offered using the Proxy SG 6.6 solution. This an introductory course and is designed for ... |
|
Register |

|
IMPLEMENTING CISCO EDGE NETWORK SECURITY SOLUTIONSThis course has been designed to provide students with the knowledge and skills required to implement and manage security on Cisco ASA firewalls, Cisco Routers with the firewall feature set and Cisco Switches. Students w ... |
|
Register |

|
JUNOS INTRUSION PREVENTION SYSTEM FUNCTIONALITYThe Junos Intrusion prevention System Functionality (JIPS) course is designed to provide an introduction to the Intrusion Prevention System (IPS) feature set available on the Juniper Networks SRX Series Services Gateway. ... |
|
Register |

|
CERTIFIED CHIEF INFORMATION SECURITY OFFICEREC-Council’s CCISO Program has certified leading information security professionals around the world. A core group of high-level information security executives, the CCISO Advisory Board, contributed by forming the found ... |
|
Register |

|
IBM ACCESS MANAGER PLATFORM FOUNDATIONSIBM Access Manager is a highly scalable and configurable access management solution. It simplifies and secures your user experience with single sign-on across applications and protects critical assets using strong multi- ... |
|
Register |

|
VMWARE NSX-T DATA CENTER: INSTALL, CONFIGURE, MANAGEThis five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T™ Data Center environment. This course covers key NSX-T Data Center features and functionality offer ... |
|
Register |

|
SYMANTEC ASSET MANAGEMENT SUITE 8.5 ADMINISTRATIONThe Symantec Asset Management Suite 8.5 Administration course is designed for professionals tasked with using Symantec Asset Management Suite (AMS) to manage their software and hardware resources in their organizations. ... |
|
Register |

|
SYMANTEC CONTROL COMPLIANCE SUITE 12.0 ADMINISTRATIONThe Control Compliance Suite 12.0 Administration course is designed for professionals who are tasked with ensuring the security of their computing enterprise and compliance with both external and internal mandates. This ... |
|
Register |

|
SYMANTEC ENDPOINT ENCRYPTION 11.2 INSTALL, CONFIGURE AND DEPLOYThe Symantec Endpoint Encryption 11.2: Install, Configure, and Deploy course is designed for the network, IT security, systems administration, and support professional tasked with maintaining and troubleshooting a Symant ... |
|
Register |

|
EC-COUNCIL NETWORK SECURITY ADMINISTRATORThis course looks at the network security in defensive view. The ENSA program is designed to provide fundamental skills needed to analyze the internal and external security threats against a network, and to develop secur ... |
|
Register |

|
IMPLEMENTING AND CONFIGURING CISCO IDENTITY SERVICES ENGINEThe Implementing and Configuring Cisco Identity Services Engine course shows you how to deploy and use Cisco Identity Services Engine (ISE) v2.4, an identity and access control policy platform that simplifies the deliver ... |
|
Register |

|
EC-COUNCIL CERTIFIED ENCRYPTION SPECIALISTThe EC-Council Certified Encryption Specialist (ECES) program introduces professionals and students to the field of cryptography. The participants will learn the foundations of modern symmetric and key cryptography inclu ... |
|
Register |

|
CISCO ASA WITH FIREPOWER SERVICES WORKSHOPThe Cisco Next-Generation Firewall (NGFW) is the industry’s first fully integrated, threat-focused NGFW. It delivers comprehensive, unified policy management of firewall functions, application control, threat prevention, ... |
|
Register |

|
DEEP SECURITY TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro™ Deep Security. This course provides information about the basic architecture, deployment scenarios, installation processes, policy configuration and administration o ... |
|
Register |

|
CompTIA Security+CompTIA Security+ (SY0-601) is a course designed to teach IT professionals the fundamentals of information security. The course covers everything from basic security concepts to advanced topics like identity management a ... |
|
Register |
Bahrain , Manama |
|||
|---|---|---|---|

|
EC-COUNCIL CERTIFIED SECURITY ANALYST V.10The ECSA program offers a seamless learning progress continuing where the CEH program left off. The new ECSAv10 includes updated curricula and an industry recognized comprehensive step-by step penetration testing method ... |
|
Register |

|
IBM ACCESS MANAGER PLATFORM FOUNDATIONSIBM Access Manager is a highly scalable and configurable access management solution. It simplifies and secures your user experience with single sign-on across applications and protects critical assets using strong multi- ... |
|
Register |

|
MANAGING ENTERPRISE SECURITY WITH CISCO SECURITY MANAGERThe Managing Enterprise Security with Cisco Security Manager (SSECMGT) course is aimed at providing network security engineers with the knowledge and skills that are needed to configure and deploy Cisco Security Manager. ... |
|
Register |

|
IMPLEMENTING FOREFRONT IDENTITY MANAGER 2010This four-day instructor-led course introduces and explains the features and capabilities of Microsoft Forefront Identity Manager 2010 (FIM), and provides an overview of the solution scenarios that FIM addresses. The cou ... |
|
Register |
|
|
CYBER SEC FIRST RESPONDER™ (CFR) CERTIFICATIONThis course covers network defense and incident response methods, tactics, and procedures are taught in alignment with industry frameworks such as NIST 800-61 r.2 (Computer Security Incident Handling), US-CERT’s NCISP (N ... |
|
Register |

|
SYMANTEC DEPLOYMENT SOLUTION 8.1 ADMINISTRATIONThe Symantec Deployment Solution 8.1: Administration course is designed for the professional tasked with installing, configuring, and managing a Deployment Solution system. This five-day, instructor-led, hands-on course ... |
|
Register |

|
COMPTIA CSA+ CYBERSECURITY ANALYSTThe CompTIA CSA+ certification is a vendor-neutral credential. The CompTIA CSA+ exam (Exam CS0-001) is an internationally targeted validation of intermediate-level security skills and knowledge. The course has a technica ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.5: ADMINISTRATIONThe Symantec Messaging Gateway 10.5: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This three-day, instructor-led, hands-on cl ... |
|
Register |

|
RHS333-BUNDLE: RED HAT ENTERPRISE SECURITY: NETWORK SERVICES + EX333Red Hat® Enterprise Security: Network Services with Exam is an intensive course that provides 4 days of instruction and labs that show students how to use the latest technologies to secure services. This class advances b ... |
|
Register |

|
COMPUTER HACKING FORENSICS INVESTIGATORThe CHFI course will give participants the necessary skills to identify an intruder's footprints and to properly gather the necessary evidence to prosecute. Many of today's top tools of the forensic trade will be taught ... |
|
Register |

|
NSX-T: INSTALL, CONFIGURE, MANAGEThis five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T™ Data Center environment. This course covers key NSX-T Data Center features and functionality offer ... |
|
Register |

|
JUNOS SECURITYThis five-day course covers the configuration, operation, and implementation of SRX Series Services Gateways in a typical network environment. Key topics within this course include: security zones, security policies, Net ... |
|
Register |

|
BLUE COAT CERTIFIED SECURITY ANALYTICS ADMINISTRATORThe Blue Coat Certified Security Analytics Administrator (BCSAA) course is intended for IT professionals who want to master the fundamentals of the Blue Coat Security Analytics solution. |
|
Register |

|
ADVANCED JUNOS SECURITYThis five-day course, which is designed to build off the current Junos Security (JSEC) offering, delves deeper into Junos security and next-generation security features. Through demonstrations and hands-on labs, you will ... |
|
Register |

|
DEPLOYING AND MANAGING WINDOWS 10 USING ENTERPRISE SERVICESThis 5-day course provides administrators with the knowledge and skills needed to deploy and manage Windows 10 desktops, devices, and applications in an enterprise environment. Students learn how to plan and implement Wi ... |
|
Register |
 CERTIFICATION44.jpg)
|
CERTIFIED INTERNET OF THINGS PRACTITIONER (CIOTP) CERTIFICATIONThe Internet of Things (IoT) promises a wide range of benefits for industry, energy and utility companies, municipalities, healthcare, and consumers. Data can be collected in extraordinary volume and detail regarding alm ... |
|
Register |
|
SYMANTEC SECURITY ANALYTICS 7.2.X ADMINISTRATORThe Symantec Security Analytics Administrator course is intended for IT professionals who want to master the fundamentals of the Symantec Security Analytics solution. Hands-On This course includes practical hands-on exe ... |
|
Register |

|
SYMANTEC CLIENT MANAGEMENT SUITE 8.5 ADMINISTRATIONThe Client Management Suite 8.5 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |

|
IBM IDENTITY GOVERNANCE AND INTELLIGENCE FOUNDATIONSIBM Identity Governance and Intelligence is an advanced identity governance system. This course provides the foundational skills necessary to operate, administer, and accomplish the major business functions and analyses ... |
|
Register |

|
IMPLEMENTING AND CONFIGURING CISCO IDENTITY SERVICES ENGINEThe Implementing and Configuring Cisco Identity Services Engine course shows you how to deploy and use Cisco Identity Services Engine (ISE) v2.4, an identity and access control policy platform that simplifies the deliver ... |
|
Register |

|
IMPLEMENTING CISCO THREAT CONTROL SYSTEMSImplementing Cisco Threat Control Solutions is designed to provide security engineers with the knowledge and hands-on experience required to deploy Cisco’s Email Security (ESA); Web Security (CWS, WSA); Advanced Malware ... |
|
Register |

|
SYMANTEC NETBACKUP 7.5: MAINTAIN AND TROUBLESHOOTThe three day Symantec Net Backup Maintain and Troubleshoot course provides the IT professional with instruction on troubleshooting Symantec NetBackup 7.5 software. This course covers general error detection tools and t ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 15.0 ADMINISTRATIONThe Symantec Data Loss Prevention 15.0 Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands-on labs inc ... |
|
Register |

|
NETWORK AND SECURITY MANAGER FUNDAMENTALSThis two-day course discusses the basic operations of Network and Security Manager. Key topics include server and domain administration, device configuration, template creation and management, policy creation and managem ... |
|
Register |

|
SECURITY FUNDAMENTALSIn this course, you will be introduced to security concepts for today's business and technology professionals. You will cover layered security philosophy, physical security, Internet security, and wireless security princ ... |
|
Register |

|
CERTIFIED IN RISK AND INFORMATION SYSTEMS CONTROLThe CRISC Review Manual and CRISC Review, Questions, Answers and Explanation Manual will be provided to delegates booked on the course. |
|
Register |

|
IBM SECURITY IDENTITY MANAGER FOUNDATIONSThis is an instructor-led course that introduces students to the foundational skills required to install, configure, and administer IBM Security Identity Manager,. IBM Security Identity Manager can be deployed using the ... |
|
Register |

|
SYMANTEC SECURITY ANALYTICS 7.2.X ADMINISTRATORThe Symantec Security Analytics Administrator course is intended for IT professionals who want to master the fundamentals of the Symantec Security Analytics solution. Hands-On This course includes practical hands-on exe ... |
|
Register |

|
SYMANTEC IT MANAGEMENT SUITE 8.1 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec IT Management Suite 8.1 Diagnostics and Troubleshooting course is designed for professionals tasked with maintaining and utilizing a Symantec IT Management Suite (ITMS) implementation in their organizations. ... |
|
Register |

|
RED TEAM VS BLUE TEAM CYBERWAR CHALLENGETwo Teams, two different approaches, Red Team vs Blue Team Cyberwar Challenge! The cyber kill chain - reconnaissance, attack planning and delivery, system exploitation, privilege escalation and lateral movement, anomalie ... |
|
Register |

|
IMPLEMENTING AND MANAGING WINDOWS 10This course is designed to provide students with the knowledge and skills required to install and configure Windows 10 desktops and devices in a Windows Server domain corporate environment. These skills include learning ... |
|
Register |

|
EC - COUNCIL CERTIFIED SECURE PROGRAMMERSoftware defects, bugs, and flaws in the logic of the program are consistently the cause for software vulnerabilities. Analysis by software security professionals has proven that most vulnerabilities are due to errors i ... |
|
Register |

|
WEB SECURITY SERVICE 6.10 DIAGNOSTICS AND TROUBLESHOOTINGThe WSS Diagnostics and Troubleshooting course is intended for IT professionals who will be diagnosing and troubleshooting the Symantec Web Security Service (WSS). |
|
Register |

|
Protecting Against Malware Threats with Cisco AMP for EndpointsThis lab-intensive course introduces students to the powerful features of Cisco AMP for Endpoints software. A number of step by step attack scenarios will provide an understanding of the operational uses of the product. ... |
|
Register |

|
CompTIA Pentest +As organizations scramble to protect themselves and their customers against privacy or security breaches, the ability to conduct penetration testing is an emerging skill set that is becoming ever more valuable to the org ... |
|
Register |

|
VMWARE NSX-T DATA CENTER: INSTALL, CONFIGURE, MANAGEThis five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T™ Data Center environment. This course covers key NSX-T Data Center features and functionality offer ... |
|
Register |

|
SYMANTEC DATA CENTER SECURITY SERVER ADVANCED 6.7 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec Data Center Server Advanced 6.7 Diagnostics and Troubleshooting course is designed for the IT security management professional tasked with troubleshooting Data Center Security Server Advanced (SDCSSA). Stud ... |
|
Register |

|
SYMANTEC PROXY SG V6.6: BASIC ADMINISTRATIONThe Proxy SG 6.6 Basic Administration course is an introduction to deployment options and management of the individual key features offered using the Proxy SG 6.6 solution. This an introductory course and is designed for ... |
|
Register |

|
CERTIFIED INFORMATION SECURITY MANAGERFive years of experience with audit, IT systems, and security of information systems; systems administration experience; familiarity with TCP/IP; and an understanding of UNIX, Linux, and Windows. This advanced course als ... |
|
Register |

|
EC-COUNCIL CERTIFIED INCIDENT HANDLERThe EC-Council Certified Incident Handler (ECIH) program is designed to provide the fundamental skills to handle and respond to the computer security incidents in an information system. The course addresses various under ... |
|
Register |

|
CISSP CERTIFICATION PREP COURSE V1.0Gain core knowledge and experience to successfully implement and manage security programs and prepare for the CISSP certification. This course is the most comprehensive review of information security concepts and industr ... |
|
Register |

|
TREND MICRO APEX ONE TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro Apex One™. This course details basic architecture, protection functionality, deployment scenarios, and troubleshooting. Through hands-on labs, participants practice c ... |
|
Register |

|
SYMANTEC PROXY SG V6.6: ADVANCED ADMINISTRATIONThe Proxy SG v6.6 Advanced Administration course is intended for IT professionals who wish to learn to master the advanced features of Proxy SG. |
|
Register |

|
MASTER CLASS ISO 27001 IMPLEMENTATIONThis five-day intensive course enables the participants to develop the expertise to support an organization in implementing and managing an Information Security Management System (ISMS) as specified in ISO/IEC 27001:2013 ... |
|
Register |
.png)
|
FIREWALL 8.1: OPTIMIZING FIREWALL THREAT PREVENTION (EDU-214)Successful completion of this four-day, instructor-led course will enhance the student’s understanding of how to better configure, manage, and monitor PAN-OS® threat prevention features. The student will get hands-on exp ... |
|
Register |
South Africa , Cape Town |
|||
|---|---|---|---|

|
SYMANTEC SECURITY ANALYTICS 7.2.X PROFESSIONALThe Symantec Security Analytics Professional course is designed for participants who want to learn how to use the Symantec Security Analytics platform to perform virtually any type of network-based monitoring and forensi ... |
|
Register |
Turkey , Istanbul |
|||
|---|---|---|---|

|
UNDERSTANDING CISCO CYBER SECURITY FUNDAMENTALSThe Understanding Cisco Cyber security Fundamentals (SECFND) v1.0 course provides you with an understanding of network infrastructure devices, operations and vulnerabilities of the TCP/IP protocol suite, basic informatio ... |
|
Register |

|
Certified Threat Intelligence AnalystCertified Threat Intelligence Analyst (C|TIA) is a training and credentialing program designed and developed in collaboration with cybersecurity and threat intelligence experts across the globe to help organizations iden ... |
|
Register |

|
Protecting Against Malware Threats with Cisco AMP for EndpointsThis lab-intensive course introduces students to the powerful features of Cisco AMP for Endpoints software. A number of step by step attack scenarios will provide an understanding of the operational uses of the product. ... |
|
Register |

|
EC-COUNCIL CERTIFIED ENCRYPTION SPECIALISTThe EC-Council Certified Encryption Specialist (ECES) program introduces professionals and students to the field of cryptography. The participants will learn the foundations of modern symmetric and key cryptography inclu ... |
|
Register |

|
SECURING NETWORKS WITH FIREPOWER THREAT DEFENSE NGFWThe Securing Networks with Cisco Firepower Threat Defense NGFW (FIREPOWER200) course demonstrates the powerful features of Cisco Firepower Threat Defense, including VPN configuration, traffic control, NAT configuration, ... |
|
Register |

|
CLIENT MANAGEMENT SUITE 8.1 ADMINISTRATIONThe Client Management Suite 8.1 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |

|
SYMANTEC DATA CENTER SECURITY SERVER ADVANCED 6.7 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec Data Center Server Advanced 6.7 Diagnostics and Troubleshooting course is designed for the IT security management professional tasked with troubleshooting Data Center Security Server Advanced (SDCSSA). Stud ... |
|
Register |

|
Implementing Forefront Unified Access Gateway 2010This three-day instructor-led course prepares you to design and deploy remote access solutions using Microsoft Forefront Unified Access Gateway 2010 (UAG). Forefront UAG provides organizations with unparalleled flexibili ... |
|
Register |
.jpg)
|
PANORAMA 8.1: MANAGING FIREWALLS AT SCALE (EDU-220)This course will help students to gain in-depth knowledge about how to configure and manage their Palo Alto Networks® Panorama TM management server. Upon completion of this course, administrators should be familiar with ... |
|
Register |
.jpg)
|
RED HAT SECURITY: LINUX IN PHYSICAL, VIRTUAL, AND CLOUD WITH EXAM (EX415)Maintaining security of computing systems is a process of managing risk through the implementation of processes and standards backed by technologies and tools. In this course, you will learn about resources that can be u ... |
|
Register |

|
MASTER CLASS ISO 27001 IMPLEMENTATIONThis five-day intensive course enables the participants to develop the expertise to support an organization in implementing and managing an Information Security Management System (ISMS) as specified in ISO/IEC 27001:2013 ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS AUDITORCISA® is a trademark of the Information Systems Audit and Control Association® (ISACA®) More than 60,000 security professionals hold CISA certification, which was awarded the "Best Professional Certification" for 2009 b ... |
|
Register |

|
IMPLEMENTING AND MANAGING WINDOWS 10This course is designed to provide students with the knowledge and skills required to install and configure Windows 10 desktops and devices in a Windows Server domain corporate environment. These skills include learning ... |
|
Register |

|
SYMANTEC ASSET MANAGEMENT SUITE 8.5 ADMINISTRATIONThe Symantec Asset Management Suite 8.5 Administration course is designed for professionals tasked with using Symantec Asset Management Suite (AMS) to manage their software and hardware resources in their organizations. ... |
|
Register |

|
COMPTIA CSA+ CYBERSECURITY ANALYSTThe CompTIA CSA+ certification is a vendor-neutral credential. The CompTIA CSA+ exam (Exam CS0-001) is an internationally targeted validation of intermediate-level security skills and knowledge. The course has a technica ... |
|
Register |
.jpg)
|
EC-COUNCIL CERTIFIED SOC ANALYST (CSA)The Certified SOC Analyst (CSA) program is the first step to joining a security operations center (SOC). It is engineered for current and aspiring Tier I and Tier II SOC analysts to achieve proficiency in performing entr ... |
|
Register |

|
SYMANTEC IT MANAGEMENT SUITE 8.1 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec IT Management Suite 8.1 Diagnostics and Troubleshooting course is designed for professionals tasked with maintaining and utilizing a Symantec IT Management Suite (ITMS) implementation in their organizations. ... |
|
Register |

|
SECURING CISCO NETWORKS WITH OPEN SOURCE SNORTSecuring Cisco Networks with Open Source Snort is a lab-intensive course that introduces students to the open source Snort technology as well as rule writing. You will learn how to build and manage a Snort system using o ... |
|
Register |

|
BLUE COAT CERTIFIED PROXY PROFESSIONALIn the Blue Coat Certified Proxy Professional (BCCPP) course, you will learn to configure your Blue Coat Proxy appliance for high availability and multi-site deployments, advance policy features, web content control, P2P ... |
|
Register |
.jpg)
|
CISCO CCNA SECURITY BOOT CAMP (ACCELERATED)In this course, you will learn how to install, operate, configure, and verify a basic IPv4 and IPv6 network, including configuring a LAN switch, configuring an IP router, managing network devices. You will also learn abo ... |
|
Register |

|
ADVANCED JUNOS SECURITYThis five-day course, which is designed to build off the current Junos Security (JSEC) offering, delves deeper into Junos security and next-generation security features. Through demonstrations and hands-on labs, you will ... |
|
Register |

|
RED HAT SERVER HARDENINGSecure a Red Hat Enterprise Linux system to comply with security policy requirements Red Hat® Server Hardening (RH413) builds on a student's Red Hat Certified Engineer (RHCE®) certification or equivalent experience to t ... |
|
Register |

|
DEPLOYING AND MANAGING WINDOWS 10 USING ENTERPRISE SERVICESThis 5-day course provides administrators with the knowledge and skills needed to deploy and manage Windows 10 desktops, devices, and applications in an enterprise environment. Students learn how to plan and implement Wi ... |
|
Register |

|
IMPLEMENTING FOREFRONT IDENTITY MANAGER 2010This four-day instructor-led course introduces and explains the features and capabilities of Microsoft Forefront Identity Manager 2010 (FIM), and provides an overview of the solution scenarios that FIM addresses. The cou ... |
|
Register |

|
IBM DIRECTORY SERVER 6.4 FUNDAMENTALSThis course describes the processes, procedures, and practices necessary to configure and administer IBM Directory Server. During the hand-on exercises, students will perform basic Directory Server configuration, setup r ... |
|
Register |

|
SECURING CISCO NETWORKS WITH SNORT RULE WRITING BEST PRACTICESSecuring Cisco Networks with Snort Rule Writing Best Practices is a lab-intensive course that introduces students to the open source Snort community and rule-writing best practices. Users focus exclusively on the Snort r ... |
|
Register |

|
SYMANTEC SECURITY ANALYTICS 7.2.X ADMINISTRATORThe Symantec Security Analytics Administrator course is intended for IT professionals who want to master the fundamentals of the Symantec Security Analytics solution. Hands-On This course includes practical hands-on exe ... |
|
Register |

|
IMPLEMENTING ADVANCED CISCO ASA SECURITY V2.0This course provides up-to-date training on the key features of the Cisco ASA 5500-X Series next-Generation Firewall, including ASAv, ASA IDFW, ASA Fire POWER Service Module, ASA Cloud Web Security and ASA Clustering. Ex ... |
|
Register |

|
IBM IDENTITY GOVERNANCE AND INTELLIGENCE FOUNDATIONSIBM Identity Governance and Intelligence is an advanced identity governance system. This course provides the foundational skills necessary to operate, administer, and accomplish the major business functions and analyses ... |
|
Register |

|
CONFIGURING AND DEPLOYING A PRIVATE CLOUDThis course equips students with the skills they require to configure and deploy a cloud using Microsoft System Center 2012 R2. Using hands-on labs, students learn the following: - Produce a high-level design that acc ... |
|
Register |

|
TREND MICRO DEEP DISCOVERY TRAINING FOR CERTIFIED PROFESSIONALSTrend Micro™ Deep Discovery Training for Certified Professionals is a three-day, instructor-led training course where participants will learn how to deploy and manage a Trend Micro™ Deep Discovery threat protection solut ... |
|
Register |

|
IMPLEMENTING CISCO NETWORK SECURITY V3.0This is a five-day instructor-led course that focuses on the design, implementation and monitoring of a comprehensive security policy, using Cisco IOS security features and technologies. All IOS examples and hands on exp ... |
|
Register |

|
WORKSHOP: WINDOWS SERVER 2019Learn about the new enhanced capabilities of the Windows 2019 starting from server virtualization, storage, software-defined networking, server management and automation, web and application platform, access to informati ... |
|
Register |

|
IMPLEMENTING CISCO THREAT CONTROL SYSTEMSImplementing Cisco Threat Control Solutions is designed to provide security engineers with the knowledge and hands-on experience required to deploy Cisco’s Email Security (ESA); Web Security (CWS, WSA); Advanced Malware ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.6 ADMINISTRATIONThe Symantec Messaging Gateway 10.6: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This two-day, instructor-led, hand son clas ... |
|
Register |

|
DEV SEC OPS ENGINEERINGA Dev Sec Ops Engineer is an IT Security professional who is skilled at “security as code” with the intent of making security and compliance consumable as a service. A Dev Sec Ops Engineer uses data and security science ... |
|
Register |

|
IMPLEMENTING CISCO CYBERSECURITY OPERATIONSThis is the second course in Cisco's CCNA Cyber Ops Curriculum and is designed to provide students with an understanding of how a Security Operations Center (SOC) functions and the knowledge required in this environment. ... |
|
Register |

|
Channel Partner Securing Email with Cisco Email Security ApplianceThis course is designed to help learners understand how to install, configure, and manage the Cisco Email Security Appliance in a small to medium-sized business and enterprise installation. Knowledge application and basi ... |
|
Register |

|
TREND MICRO APEX ONE TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro Apex One™. This course details basic architecture, protection functionality, deployment scenarios, and troubleshooting. Through hands-on labs, participants practice c ... |
|
Register |

|
Blue Coat Certified Proxy AdministratorThe Blue Coat Certified Proxy SG Professional (BCCPP) Course is intended for IT professionals who wish to master the advance features of the Blue Coat Proxy SG. |
|
Register |

|
CISCO ASA WITH FIREPOWER SERVICES WORKSHOPThe Cisco Next-Generation Firewall (NGFW) is the industry’s first fully integrated, threat-focused NGFW. It delivers comprehensive, unified policy management of firewall functions, application control, threat prevention, ... |
|
Register |

|
JUNOS SPACE-SECURITY DIRECTORThis two-day course is designed to provide students with the knowledge required to manage the Junos Space Security Director application and manage devices with that application. Students will gain in-depth knowledge of h ... |
|
Register |

|
SYMANTEC SSL VISIBILITY 5.0 ADMINISTRATIONThe SSL Visibility 5.0 Administration course enables you to plan, implement, configure and managed your SSLV virtual appliance. This course includes both lecture and hands-on labs that access the SSLV virtual appliance. ... |
|
Register |

|
RED HAT SECURITY: SECURING CONTAINERS AND OPEN SHIFT WITH EXAMYou will learn and validate your skills in using secure and trusted container images, registries, and source code; managing network and storage isolation; implementing application single sign-on; and configuring appropri ... |
|
Register |

|
JNCIE-SEC BOOT CAMPThis five-day course is designed to serve as the ultimate preparation for the Juniper Networks Certified Internet Expert—Security (JNCIE-SEC) exam. The course focuses on caveats and tips useful for potential test candida ... |
|
Register |
|
|
CYBER SEC FIRST RESPONDER™ (CFR) CERTIFICATIONThis course covers network defense and incident response methods, tactics, and procedures are taught in alignment with industry frameworks such as NIST 800-61 r.2 (Computer Security Incident Handling), US-CERT’s NCISP (N ... |
|
Register |

|
SYMANTEC CONTROL COMPLIANCE SUITE 12.0 ADMINISTRATIONThe Control Compliance Suite 12.0 Administration course is designed for professionals who are tasked with ensuring the security of their computing enterprise and compliance with both external and internal mandates. This ... |
|
Register |

|
SECURITY FUNDAMENTALSIn this course, you will be introduced to security concepts for today's business and technology professionals. You will cover layered security philosophy, physical security, Internet security, and wireless security princ ... |
|
Register |

|
PERFORMANCE TUNING AND OPTIMIZING SQL DATABASESThis four-day instructor-led course provides students who manage and maintain SQL Server databases with the knowledge and skills to performance tune and optimize their databases. |
|
Register |

|
SYMANTEC DEPLOYMENT SOLUTION 8.1 ADMINISTRATIONThe Symantec Deployment Solution 8.1: Administration course is designed for the professional tasked with installing, configuring, and managing a Deployment Solution system. This five-day, instructor-led, hands-on course ... |
|
Register |

|
EC-COUNCIL CERTIFIED SECURITY ANALYST V.10The ECSA program offers a seamless learning progress continuing where the CEH program left off. The new ECSAv10 includes updated curricula and an industry recognized comprehensive step-by step penetration testing method ... |
|
Register |

|
CompTIA Pentest +As organizations scramble to protect themselves and their customers against privacy or security breaches, the ability to conduct penetration testing is an emerging skill set that is becoming ever more valuable to the org ... |
|
Register |

|
CERTIFIED IN THE GOVERNANCE OF ENTERPRISE ITAs technology has become more and more vital to the achievement of business goals and value delivery, enterprise leaders have realized that enterprise governance must be extended to information technology and information ... |
|
Register |

|
IMPLEMENTING CISCO UNIFIED COMMUNICATIONS SECURITYThe Implementing Cisco Unified Communications Security (UCSEC) course is designed to provide students with the necessary knowledge and skills to implement security features in a Cisco Unified Communications environment. ... |
|
Register |

|
SYMANTEC PROXY SG V6.6: ADVANCED ADMINISTRATIONThe Proxy SG v6.6 Advanced Administration course is intended for IT professionals who wish to learn to master the advanced features of Proxy SG. |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 15.5 ADMINISTRATIONThe Symantec Data Loss Prevention 15.5 Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands‐on labs inc ... |
|
Register |

|
BLUE COAT CERTIFIED SECURITY ANALYTICS ADMINISTRATORThe Blue Coat Certified Security Analytics Administrator (BCSAA) course is intended for IT professionals who want to master the fundamentals of the Blue Coat Security Analytics solution. |
|
Register |

|
EC-COUNCIL CERTIFIED NETWORK DEFENDERCertified Network Defender (CND) is a vendor-neutral, hands-on, instructor-led comprehensive network security certification training program. It is a skills-based, lab intensive program based on a job-task analysis and c ... |
|
Register |

|
MANAGING ENTERPRISE SECURITY WITH CISCO SECURITY MANAGERThe Managing Enterprise Security with Cisco Security Manager (SSECMGT) course is aimed at providing network security engineers with the knowledge and skills that are needed to configure and deploy Cisco Security Manager. ... |
|
Register |

|
IBM DIRECTORY SERVER 6.4 FUNDAMENTALSThis course describes the processes, procedures, and practices necessary to configure and administer IBM Directory Server. During the hand-on exercises, students will perform basic Directory Server configuration, setup r ... |
|
Register |
Malaysia , Kuala-Lumpur |
|||
|---|---|---|---|

|
IBM GUARDIUM FOUNDATIONSAre you getting ready to administer database security policies? Learn how to configure Guardium to discover, classify, analyze, protect, and control access to sensitive data. You learn to perform vulnerability assessment ... |
|
Register |

|
SECURITY+The Security+ Certification Prep Course provides the basic knowledge needed to plan, implement, and maintain information security in a vendor-neutral format. This includes risk management, host and network security, auth ... |
|
Register |
.jpg)
|
CISCO CCNA SECURITY BOOT CAMP (ACCELERATED)In this course, you will learn how to install, operate, configure, and verify a basic IPv4 and IPv6 network, including configuring a LAN switch, configuring an IP router, managing network devices. You will also learn abo ... |
|
Register |

|
EC-COUNCIL CERTIFIED NETWORK DEFENDERCertified Network Defender (CND) is a vendor-neutral, hands-on, instructor-led comprehensive network security certification training program. It is a skills-based, lab intensive program based on a job-task analysis and c ... |
|
Register |

|
CERTIFIED IN RISK AND INFORMATION SYSTEMS CONTROLThe CRISC Review Manual and CRISC Review, Questions, Answers and Explanation Manual will be provided to delegates booked on the course. |
|
Register |

|
CERTIFIED INFORMATION SECURITY MANAGERFive years of experience with audit, IT systems, and security of information systems; systems administration experience; familiarity with TCP/IP; and an understanding of UNIX, Linux, and Windows. This advanced course als ... |
|
Register |

|
SECURING CISCO NETWORKS WITH SOURCE FIRE INTRUSION PREVENTION SYSTEMThe Securing Networks with Cisco Firepower Next-Generation IPS course shows you how to deploy and use Cisco Firepower Next-Generation Intrusion Prevention System (NGIPS). This hands-on course gives you the knowledge and ... |
|
Register |
 CERTIFICATION.png)
|
CYBER SECURE CODER (CSC) CERTIFICATIONThe stakes for software security are very high, and yet many development teams deal with software security only after the code has been developed and the software is being prepared for delivery. As with any aspect of sof ... |
|
Register |

|
DEEP SECURITY TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro™ Deep Security. This course provides information about the basic architecture, deployment scenarios, installation processes, policy configuration and administration o ... |
|
Register |

|
SYMANTEC SSL VISIBILITY 5.0 ADMINISTRATIONThe SSL Visibility 5.0 Administration course enables you to plan, implement, configure and managed your SSLV virtual appliance. This course includes both lecture and hands-on labs that access the SSLV virtual appliance. ... |
|
Register |

|
EC - COUNCIL CERTIFIED SECURE PROGRAMMERSoftware defects, bugs, and flaws in the logic of the program are consistently the cause for software vulnerabilities. Analysis by software security professionals has proven that most vulnerabilities are due to errors i ... |
|
Register |

|
BLUE COAT CERTIFIED SECURITY ANALYTICS PROFESSIONALThe Blue Coat Certified Security Analytics Professional (BCSAP) course designed for participants who want to learn how to use the Blue Coat Security Analytics platform to perform virtually any type of network-based monit ... |
|
Register |

|
IMPLEMENTING CISCO UNIFIED COMMUNICATIONS SECURITYThe Implementing Cisco Unified Communications Security (UCSEC) course is designed to provide students with the necessary knowledge and skills to implement security features in a Cisco Unified Communications environment. ... |
|
Register |

|
IBM SECURITY QRADAR SIEM ADVANCED TOPICSThis is an advanced course for the QRadar Analyst and Administrator and is a follow-on to BQ103G. This course uses the IBM QRadar SIEM 7.3 platform for lab exercises. |
|
Register |

|
SYMANTEC NET BACKUP 7.6.X: ADMINISTRATIONThis Symantec Net Backup 7.6.x: Administration course provides the IT professional with instruction on the functionality of Symantec NetBackup 7.6.1 software. This course covers the general principles of using NetBackup ... |
|
Register |

|
MANAGING AND DEFENDING AGAINST CURRENT THREATSThis is a deep dive course on security operations: vulnerability management, anomalies detection, discovery of industry attacks and threats, understanding how compromised system or solution looks like, defining the indic ... |
|
Register |
.png)
|
FIREWALL 8.1: OPTIMIZING FIREWALL THREAT PREVENTION (EDU-214)Successful completion of this four-day, instructor-led course will enhance the student’s understanding of how to better configure, manage, and monitor PAN-OS® threat prevention features. The student will get hands-on exp ... |
|
Register |

|
NSX-T: INSTALL, CONFIGURE, MANAGEThis five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T™ Data Center environment. This course covers key NSX-T Data Center features and functionality offer ... |
|
Register |

|
SYMANTEC CLIENT MANAGEMENT SUITE 8.5 ADMINISTRATIONThe Client Management Suite 8.5 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |
 CERTIFICATION44.jpg)
|
CERTIFIED INTERNET OF THINGS PRACTITIONER (CIOTP) CERTIFICATIONThe Internet of Things (IoT) promises a wide range of benefits for industry, energy and utility companies, municipalities, healthcare, and consumers. Data can be collected in extraordinary volume and detail regarding alm ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.5: ADMINISTRATIONThe Symantec Messaging Gateway 10.5: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This three-day, instructor-led, hands-on cl ... |
|
Register |

|
MASTERCLASS: PEN TESTING AND SECURING MOBILE AND WEB APPLICATIONSThe course teaches mobile and web application security concepts, including the techniques on how to attack and how to respond with an appropriate countermeasure implementation. Our course has been developed around profes ... |
|
Register |

|
SYMANTEC SECURITY ANALYTICS 7.2.X PROFESSIONALThe Symantec Security Analytics Professional course is designed for participants who want to learn how to use the Symantec Security Analytics platform to perform virtually any type of network-based monitoring and forensi ... |
|
Register |

|
SYMANTEC ENDPOINT ENCRYPTION 11.2 INSTALL, CONFIGURE AND DEPLOYThe Symantec Endpoint Encryption 11.2: Install, Configure, and Deploy course is designed for the network, IT security, systems administration, and support professional tasked with maintaining and troubleshooting a Symant ... |
|
Register |

|
CERTIFIED IN THE GOVERNANCE OF ENTERPRISE ITAs technology has become more and more vital to the achievement of business goals and value delivery, enterprise leaders have realized that enterprise governance must be extended to information technology and information ... |
|
Register |

|
EC-COUNCIL NETWORK SECURITY ADMINISTRATORThis course looks at the network security in defensive view. The ENSA program is designed to provide fundamental skills needed to analyze the internal and external security threats against a network, and to develop secur ... |
|
Register |
.jpg)
|
PALO ALTO NETWORKS® TRAPS™ ADVANCED ENDPOINT PROTECTION (PAN-EDU-281)This instructor-led course teaches strategies in defense against advanced threats. Successful completion of this course enables administrators to better understand the threat landscape. Students will learn the use of Pal ... |
|
Register |

|
MANAGING ENTERPRISE SECURITY WITH CISCO SECURITY MANAGERThe Managing Enterprise Security with Cisco Security Manager (SSECMGT) course is aimed at providing network security engineers with the knowledge and skills that are needed to configure and deploy Cisco Security Manager. ... |
|
Register |

|
JUNOS SECURITYThis five-day course covers the configuration, operation, and implementation of SRX Series Services Gateways in a typical network environment. Key topics within this course include: security zones, security policies, Net ... |
|
Register |

|
IBM QRADAR SIEM FOUNDATIONSIBM QRadar SIEM provides deep visibility into network, user, and application activity. It provides collection, normalization, correlation, and secure storage of events, flows, asset profiles, and vulnerabilities. QRadar ... |
|
Register |

|
SYSTEMS SECURITY CERTIFIED PRACTITIONERLooking to move up in the information security field? If you have at least one year of security experience, you qualify for the Systems Security Certified Practitioner (SSCP) certification, which offers junior security p ... |
|
Register |

|
RED TEAM VS BLUE TEAM CYBERWAR CHALLENGETwo Teams, two different approaches, Red Team vs Blue Team Cyberwar Challenge! The cyber kill chain - reconnaissance, attack planning and delivery, system exploitation, privilege escalation and lateral movement, anomalie ... |
|
Register |

|
CYBER SEC FIRST RESPONDER: THREAT DETECTION AND RESPONSEThis course covers the duties of those who are responsible for monitoring and detecting security incidents in information systems and networks, and for executing a proper response to such incidents. Depending on the size ... |
|
Register |

|
SYMANTEC IDENTITY AND AUTHENTICATION SERVICES R1The Symantec Identity and Authentication Services R1 course is designed for the IT security professional needing to develop an understanding of the principles and use cases behind the Symantec VIP Service and VIP Access ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 15.0 ADMINISTRATIONThe Symantec Data Loss Prevention 15.0 Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands-on labs inc ... |
|
Register |
.png)
|
PALO ALTO ADVANCED FIREWALL TROUBLESHOOTING (311)Advanced Firewall Troubleshooting is the next-level follow-on course to Palo Alto Networks® Essentials 1: Installation, Configuration, and Management (PAN-EDU-201) and Essentials 2: Extended Firewall Manager (PAN-EDU-205 ... |
|
Register |

|
SECURING EMAIL WITH CISCO EMAIL SECURITY APPLIANCEThe Securing Email with Cisco Email Security Appliance (SESA) v3.0 course shows you how to deploy and use Cisco® Email Security Appliance to establish protection for your email systems against phishing, business email co ... |
|
Register |

|
Certified Cloud Security Professional Certification PreparationAs powerful as cloud computing is for the organization, understanding its information security risks and mitigation strategies is critical. Legacy approaches are inadequate, and organizations need competent, experienced ... |
|
Register |
.jpg)
|
RED HAT IDENTITY MANAGEMENT AND ACTIVE DIRECTORY INTEGRATION WITH EXAM (EX362)This course teaches you skills on the most requested Red Hat Identity Management (IdM) capabilities, including Active Directory trusts, multi-product federation, configuration management with Ansible, integrated certific ... |
|
Register |

|
CITRIX ENTERPRISE SECURITY SOLUTIONSLearn to secure your Citrix environment in this hands-on course that encompasses the core Citrix technologies, including Citrix Virtual Apps and Desktops, ADC, Endpoint Management, Content Collaboration and Citrix Cloud. ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 15.5 ADMINISTRATIONThe Symantec Data Loss Prevention 15.5 Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands‐on labs inc ... |
|
Register |

|
COMPUTER HACKING FORENSICS INVESTIGATORThe CHFI course will give participants the necessary skills to identify an intruder's footprints and to properly gather the necessary evidence to prosecute. Many of today's top tools of the forensic trade will be taught ... |
|
Register |

|
Certified Threat Intelligence AnalystCertified Threat Intelligence Analyst (C|TIA) is a training and credentialing program designed and developed in collaboration with cybersecurity and threat intelligence experts across the globe to help organizations iden ... |
|
Register |

|
SECURING NETWORKS WITH FIREPOWER THREAT DEFENSE NGFWThe Securing Networks with Cisco Firepower Threat Defense NGFW (FIREPOWER200) course demonstrates the powerful features of Cisco Firepower Threat Defense, including VPN configuration, traffic control, NAT configuration, ... |
|
Register |

|
IMPLEMENTING ADVANCED CISCO ASA SECURITY V2.0This course provides up-to-date training on the key features of the Cisco ASA 5500-X Series next-Generation Firewall, including ASAv, ASA IDFW, ASA Fire POWER Service Module, ASA Cloud Web Security and ASA Clustering. Ex ... |
|
Register |

|
SYMANTEC DATA CENTER SECURITY SERVER ADVANCED 6.7 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec Data Center Server Advanced 6.7 Diagnostics and Troubleshooting course is designed for the IT security management professional tasked with troubleshooting Data Center Security Server Advanced (SDCSSA). Stud ... |
|
Register |

|
SECURITY FUNDAMENTALSIn this course, you will be introduced to security concepts for today's business and technology professionals. You will cover layered security philosophy, physical security, Internet security, and wireless security princ ... |
|
Register |

|
SYMANTEC WEB SECURITY SERVICE CORE ADMINISTRATION R1The Web Security Service Core Administration course is intended for IT professionals who will be installing, configuring or administering the Symantec Web Security Service (WSS). |
|
Register |

|
CONFIGURING JUNIPER NETWORKS FIREWALL/IPSEC VPN PRODUCTSThis course is the first in the Screen OS curriculum. It is a three-day, instructor-led course that focuses on configuration of the Screen OS firewall/virtual private network (VPN) products in a variety of situations, in ... |
|
Register |

|
EC-COUNCIL CERTIFIED ENCRYPTION SPECIALISTThe EC-Council Certified Encryption Specialist (ECES) program introduces professionals and students to the field of cryptography. The participants will learn the foundations of modern symmetric and key cryptography inclu ... |
|
Register |
 PREP COURSE.jpg)
|
COMPTIA ADVANCED SECURITY PRACTITIONER (CASP) PREP COURSEYou have experience in the increasingly crucial field of information security, and now you're ready to take that experience to the next level. CompTIA® Advanced Security Practitioner (CASP) (Exam CAS-002) is the course y ... |
|
Register |

|
CERTIFIED CHIEF INFORMATION SECURITY OFFICEREC-Council’s CCISO Program has certified leading information security professionals around the world. A core group of high-level information security executives, the CCISO Advisory Board, contributed by forming the found ... |
|
Register |

|
Implementing Cisco Secure MobilityThis course is designed to prepare network security engineers with the knowledge and skills they need to protect data traversing a public or shared infrastructure such as the Internet by implementing and maintaining Cisc ... |
|
Register |
.jpg)
|
LEAD AUDITOR TRAINING (IRCA CERTIFIED)This five-day intensive course enables participants to develop the expertise needed to audit an Information Security Management System (ISMS) and to manage a team of auditors by applying widely recognized audit principle ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS SECURITY PROFESSIONALThe Official (ISC)2® CISSP® CBK® Review Seminar is the most comprehensive, complete review of information systems security concepts and industry best practices, and the only review course endorsed by (ISC)2. Review Semin ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.6 ADMINISTRATIONThe Symantec Messaging Gateway 10.6: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This two-day, instructor-led, hand son clas ... |
|
Register |

|
MASTERCLASS: RED TEAM - BLUE TEAM OPERATIONSThis is a deep dive course on Red Team – Blue Team Operations: The cyber kill chain Security is a business enabler, and it is only when it is viewed from a business perspective that we can truly make the right decision ... |
|
Register |

|
Blue Coat Certified Proxy AdministratorThe Blue Coat Certified Proxy SG Professional (BCCPP) Course is intended for IT professionals who wish to master the advance features of the Blue Coat Proxy SG. |
|
Register |

|
IBM IDENTITY GOVERNANCE AND INTELLIGENCE FOUNDATIONSIBM Identity Governance and Intelligence is an advanced identity governance system. This course provides the foundational skills necessary to operate, administer, and accomplish the major business functions and analyses ... |
|
Register |

|
SYMANTEC NETBACKUP 7.5: MAINTAIN AND TROUBLESHOOTThe three day Symantec Net Backup Maintain and Troubleshoot course provides the IT professional with instruction on troubleshooting Symantec NetBackup 7.5 software. This course covers general error detection tools and t ... |
|
Register |
.jpg)
|
PANORAMA 8.1: MANAGING FIREWALLS AT SCALE (EDU-220)This course will help students to gain in-depth knowledge about how to configure and manage their Palo Alto Networks® Panorama TM management server. Upon completion of this course, administrators should be familiar with ... |
|
Register |

|
IBM GUARDIUM FOUNDATIONSAre you getting ready to administer database security policies? Learn how to configure Guardium to discover, classify, analyze, protect, and control access to sensitive data. You learn to perform vulnerability assessment ... |
|
Register |

|
UNDERSTANDING CISCO CYBER SECURITY FUNDAMENTALSThe Understanding Cisco Cyber security Fundamentals (SECFND) v1.0 course provides you with an understanding of network infrastructure devices, operations and vulnerabilities of the TCP/IP protocol suite, basic informatio ... |
|
Register |

|
RED HAT SECURITY: SECURING CONTAINERS AND OPEN SHIFT WITH EXAMYou will learn and validate your skills in using secure and trusted container images, registries, and source code; managing network and storage isolation; implementing application single sign-on; and configuring appropri ... |
|
Register |

|
Implementing Cisco Identity Services Engine for Wireless EngineersThis course has been designed to enable wireless engineers understand the concepts, architecture, and use cases of the Cisco Identity Services Engine Solution. This course provides students with the knowledge and skills ... |
|
Register |

|
SYMANTEC ASSET MANAGEMENT SUITE 8.1 ADMINISTRATIONThe Symantec Asset Management Suite 8.1 Administration course is designed for professionals tasked with using Symantec Asset Management Suite (AMS) to manage their software and hardware resources in their organizations. ... |
|
Register |
Indonesia , Indonesia |
|||
|---|---|---|---|
.jpg)
|
LEAD AUDITOR TRAINING (IRCA CERTIFIED)This five-day intensive course enables participants to develop the expertise needed to audit an Information Security Management System (ISMS) and to manage a team of auditors by applying widely recognized audit principle ... |
|
Register |

|
SYMANTEC CONTROL COMPLIANCE SUITE VULNERABILITY MANAGER 12.0 ADMINISTRATIONThe Symantec Control Compliance Suite Vulnerability Manager (CCS-VM) 12.0 Administration Training is designed for the IT security professional tasked with installation, administering, monitoring and reporting on CCS-VM 1 ... |
|
Register |

|
CYBERSECURITY FOUNDATIONSWhen you consider just a few of the consequences of a security breach - your proprietary information completely accessible, hefty fines for security lapses, news headlines about your company's security breach, it becomes ... |
|
Register |

|
BLUE COAT PACKET SHAPER PROFESSIONALBlue Coat Certified Packet Shaper Administrator (BCPSA) certification or waiver exam; student should have practical experience with the Packet Shaper appliance in the field with a solid understanding of networking and ge ... |
|
Register |
|
|
CYBER SEC FIRST RESPONDER™ (CFR) CERTIFICATIONThis course covers network defense and incident response methods, tactics, and procedures are taught in alignment with industry frameworks such as NIST 800-61 r.2 (Computer Security Incident Handling), US-CERT’s NCISP (N ... |
|
Register |

|
Implementing Cisco Identity Services Engine for Wireless EngineersThis course has been designed to enable wireless engineers understand the concepts, architecture, and use cases of the Cisco Identity Services Engine Solution. This course provides students with the knowledge and skills ... |
|
Register |

|
Implementing Cisco Secure MobilityThis course is designed to prepare network security engineers with the knowledge and skills they need to protect data traversing a public or shared infrastructure such as the Internet by implementing and maintaining Cisc ... |
|
Register |
.jpg)
|
FIREWALL 8.1: TROUBLESHOOTING (EDU-330)Successful completion of this three-day, instructor-led course will enhance the participant’s understanding of how to troubleshoot the full line of Palo Alto Networks® next-generation firewalls. Participants will have o ... |
|
Register |

|
EC-COUNCIL CERTIFIED SECURITY ANALYST V.10The ECSA program offers a seamless learning progress continuing where the CEH program left off. The new ECSAv10 includes updated curricula and an industry recognized comprehensive step-by step penetration testing method ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 14.6 ADMINISTRATIONThe Symantec Data Loss Prevention 14.X: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands-on labs i ... |
|
Register |

|
JUNOS INTRUSION PREVENTION SYSTEM FUNCTIONALITYThe Junos Intrusion prevention System Functionality (JIPS) course is designed to provide an introduction to the Intrusion Prevention System (IPS) feature set available on the Juniper Networks SRX Series Services Gateway. ... |
|
Register |

|
CISSP CERTIFICATION PREP COURSE V1.0Gain core knowledge and experience to successfully implement and manage security programs and prepare for the CISSP certification. This course is the most comprehensive review of information security concepts and industr ... |
|
Register |

|
IBM SECURITY QRADAR SIEM ADVANCED TOPICSThis is an advanced course for the QRadar Analyst and Administrator and is a follow-on to BQ103G. This course uses the IBM QRadar SIEM 7.3 platform for lab exercises. |
|
Register |

|
SECURING THE WEB WITH CISCO WEB SECURITY APPLIANCEThis course has been designed to help learners understand how to install, configure, manage, and troubleshoot a Cisco Web Security Appliance (WSA). Students will learn how to design, configure, administer, monitor, and t ... |
|
Register |

|
MASTERCLASS: RED TEAM - BLUE TEAM OPERATIONSThis is a deep dive course on Red Team – Blue Team Operations: The cyber kill chain Security is a business enabler, and it is only when it is viewed from a business perspective that we can truly make the right decision ... |
|
Register |

|
CISCO ASA EXPRESS SECURITY 1.5This course has been designed to provide an understanding of Cisco's ASA solution portfolio. Students will learn how to successfully configure various aspects of the Cisco ASA components including Cisco ASA firewall feat ... |
|
Register |

|
IMPLEMENTING AND CONFIGURING CISCO IDENTITY SERVICES ENGINEThe Implementing and Configuring Cisco Identity Services Engine course shows you how to deploy and use Cisco Identity Services Engine (ISE) v2.4, an identity and access control policy platform that simplifies the deliver ... |
|
Register |
.jpg)
|
PALO ALTO EXTENDED FIREWALL MANAGEMENT (205)Extended Firewall Management is the next-level follow-on course to Palo Alto Networks® Installation, Configuration, and Management (PAN-EDU-201). Extended Firewall Management expands on 201 course topics, while introduci ... |
|
Register |

|
SYMANTEC ASSET MANAGEMENT SUITE 8.1 ADMINISTRATIONThe Symantec Asset Management Suite 8.1 Administration course is designed for professionals tasked with using Symantec Asset Management Suite (AMS) to manage their software and hardware resources in their organizations. ... |
|
Register |

|
SYMANTEC CLOUD SOC ADMINISTRATION R2The Cloud SOC R2 Administration course provides an overview of the Cloud SOC service, covering initial setup, deployment options and service configuration. The courseware introduces each topic with an accompanying workfl ... |
|
Register |

|
CONFIGURING JUNIPER NETWORKS FIREWALL/IPSEC VPN PRODUCTSThis course is the first in the Screen OS curriculum. It is a three-day, instructor-led course that focuses on configuration of the Screen OS firewall/virtual private network (VPN) products in a variety of situations, in ... |
|
Register |

|
BLUE COAT CERTIFIED SECURITY ANALYTICS ADMINISTRATORThe Blue Coat Certified Security Analytics Administrator (BCSAA) course is intended for IT professionals who want to master the fundamentals of the Blue Coat Security Analytics solution. |
|
Register |

|
RHS333-BUNDLE: RED HAT ENTERPRISE SECURITY: NETWORK SERVICES + EX333Red Hat® Enterprise Security: Network Services with Exam is an intensive course that provides 4 days of instruction and labs that show students how to use the latest technologies to secure services. This class advances b ... |
|
Register |

|
NETWORK AND SECURITY MANAGER FUNDAMENTALSThis two-day course discusses the basic operations of Network and Security Manager. Key topics include server and domain administration, device configuration, template creation and management, policy creation and managem ... |
|
Register |

|
EC-COUNCIL CERTIFIED INCIDENT HANDLERThe EC-Council Certified Incident Handler (ECIH) program is designed to provide the fundamental skills to handle and respond to the computer security incidents in an information system. The course addresses various under ... |
|
Register |

|
CERTIFIED INFORMATION SECURITY MANAGERFive years of experience with audit, IT systems, and security of information systems; systems administration experience; familiarity with TCP/IP; and an understanding of UNIX, Linux, and Windows. This advanced course als ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS SECURITY PROFESSIONALThe Official (ISC)2® CISSP® CBK® Review Seminar is the most comprehensive, complete review of information systems security concepts and industry best practices, and the only review course endorsed by (ISC)2. Review Semin ... |
|
Register |

|
RED HAT SERVER HARDENINGSecure a Red Hat Enterprise Linux system to comply with security policy requirements Red Hat® Server Hardening (RH413) builds on a student's Red Hat Certified Engineer (RHCE®) certification or equivalent experience to t ... |
|
Register |

|
IBM DIRECTORY SERVER 6.4 FUNDAMENTALSThis course describes the processes, procedures, and practices necessary to configure and administer IBM Directory Server. During the hand-on exercises, students will perform basic Directory Server configuration, setup r ... |
|
Register |

|
SYMANTEC CLIENT MANAGEMENT SUITE 8.5 ADMINISTRATIONThe Client Management Suite 8.5 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |

|
Channel Partner Securing Email with Cisco Email Security ApplianceThis course is designed to help learners understand how to install, configure, and manage the Cisco Email Security Appliance in a small to medium-sized business and enterprise installation. Knowledge application and basi ... |
|
Register |

|
SYMANTEC NET BACKUP 7.6.X: ADMINISTRATIONThis Symantec Net Backup 7.6.x: Administration course provides the IT professional with instruction on the functionality of Symantec NetBackup 7.6.1 software. This course covers the general principles of using NetBackup ... |
|
Register |

|
SECURING CISCO NETWORKS WITH SOURCE FIRE INTRUSION PREVENTION SYSTEMThe Securing Networks with Cisco Firepower Next-Generation IPS course shows you how to deploy and use Cisco Firepower Next-Generation Intrusion Prevention System (NGIPS). This hands-on course gives you the knowledge and ... |
|
Register |

|
IMPLEMENTING CISCO EDGE NETWORK SECURITY SOLUTIONSThis course has been designed to provide students with the knowledge and skills required to implement and manage security on Cisco ASA firewalls, Cisco Routers with the firewall feature set and Cisco Switches. Students w ... |
|
Register |

|
ADVANCED JUNOS SECURITYThis five-day course, which is designed to build off the current Junos Security (JSEC) offering, delves deeper into Junos security and next-generation security features. Through demonstrations and hands-on labs, you will ... |
|
Register |

|
SYMANTEC IT MANAGEMENT SUITE 8.1 DIAGNOSTICS AND TROUBLESHOOTINGThe Symantec IT Management Suite 8.1 Diagnostics and Troubleshooting course is designed for professionals tasked with maintaining and utilizing a Symantec IT Management Suite (ITMS) implementation in their organizations. ... |
|
Register |

|
CERTIFIED SECURE COMPUTER USER - AWARENESS TRAININGThe purpose of the CSCU training program is to provide individuals with the necessary knowledge and skills to protect their information assets. This class will immerse students into an interactive environment where they ... |
|
Register |

|
SECURING EMAIL WITH CISCO EMAIL SECURITY APPLIANCEThe Securing Email with Cisco Email Security Appliance (SESA) v3.0 course shows you how to deploy and use Cisco® Email Security Appliance to establish protection for your email systems against phishing, business email co ... |
|
Register |
Nethersland , Amsterdam |
|||
|---|---|---|---|

|
IBM SECURITY IDENTITY MANAGER FOUNDATIONSThis is an instructor-led course that introduces students to the foundational skills required to install, configure, and administer IBM Security Identity Manager,. IBM Security Identity Manager can be deployed using the ... |
|
Register |

|
SYMANTEC SSL VISIBILITY 4.3 ADMINISTRATIONThe SSL Visibility 4.3 administration course enables you to plan, implement, configure and managed your SSLV appliance(s). This is a lecture-only course, there will be no hands-on access to an SSLV appliance during the c ... |
|
Register |

|
DEEP SECURITY TRAINING FOR CERTIFIED PROFESSIONALSIn this course, you will learn how to use Trend Micro™ Deep Security. This course provides information about the basic architecture, deployment scenarios, installation processes, policy configuration and administration o ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS SECURITY PROFESSIONALThe Official (ISC)2® CISSP® CBK® Review Seminar is the most comprehensive, complete review of information systems security concepts and industry best practices, and the only review course endorsed by (ISC)2. Review Semin ... |
|
Register |

|
IBM ACCESS MANAGER PLATFORM FOUNDATIONSIBM Access Manager is a highly scalable and configurable access management solution. It simplifies and secures your user experience with single sign-on across applications and protects critical assets using strong multi- ... |
|
Register |

|
MANAGING AND DEFENDING AGAINST CURRENT THREATSThis is a deep dive course on security operations: vulnerability management, anomalies detection, discovery of industry attacks and threats, understanding how compromised system or solution looks like, defining the indic ... |
|
Register |

|
EC-COUNCIL NETWORK SECURITY ADMINISTRATORThis course looks at the network security in defensive view. The ENSA program is designed to provide fundamental skills needed to analyze the internal and external security threats against a network, and to develop secur ... |
|
Register |
.jpg)
|
LEAD AUDITOR TRAINING (IRCA CERTIFIED)This five-day intensive course enables participants to develop the expertise needed to audit an Information Security Management System (ISMS) and to manage a team of auditors by applying widely recognized audit principle ... |
|
Register |
.jpg)
|
FIREWALL 8.1: TROUBLESHOOTING (EDU-330)Successful completion of this three-day, instructor-led course will enhance the participant’s understanding of how to troubleshoot the full line of Palo Alto Networks® next-generation firewalls. Participants will have o ... |
|
Register |

|
Protecting Against Malware Threats with Cisco AMP for EndpointsThis lab-intensive course introduces students to the powerful features of Cisco AMP for Endpoints software. A number of step by step attack scenarios will provide an understanding of the operational uses of the product. ... |
|
Register |

|
MASTERCLASS: RED TEAM - BLUE TEAM OPERATIONSThis is a deep dive course on Red Team – Blue Team Operations: The cyber kill chain Security is a business enabler, and it is only when it is viewed from a business perspective that we can truly make the right decision ... |
|
Register |

|
CERTIFIED IN RISK AND INFORMATION SYSTEMS CONTROLThe CRISC Review Manual and CRISC Review, Questions, Answers and Explanation Manual will be provided to delegates booked on the course. |
|
Register |

|
SECURING CISCO NETWORKS WITH OPEN SOURCE SNORTSecuring Cisco Networks with Open Source Snort is a lab-intensive course that introduces students to the open source Snort technology as well as rule writing. You will learn how to build and manage a Snort system using o ... |
|
Register |

|
IBM QRADAR SIEM FOUNDATIONSIBM QRadar SIEM provides deep visibility into network, user, and application activity. It provides collection, normalization, correlation, and secure storage of events, flows, asset profiles, and vulnerabilities. QRadar ... |
|
Register |

|
SECURING THE WEB WITH CISCO WEB SECURITY APPLIANCEThis course has been designed to help learners understand how to install, configure, manage, and troubleshoot a Cisco Web Security Appliance (WSA). Students will learn how to design, configure, administer, monitor, and t ... |
|
Register |

|
CISSP CERTIFICATION PREP COURSE V1.0Gain core knowledge and experience to successfully implement and manage security programs and prepare for the CISSP certification. This course is the most comprehensive review of information security concepts and industr ... |
|
Register |
 CERTIFICATION.png)
|
CYBER SECURE CODER (CSC) CERTIFICATIONThe stakes for software security are very high, and yet many development teams deal with software security only after the code has been developed and the software is being prepared for delivery. As with any aspect of sof ... |
|
Register |

|
Implementing Forefront Unified Access Gateway 2010This three-day instructor-led course prepares you to design and deploy remote access solutions using Microsoft Forefront Unified Access Gateway 2010 (UAG). Forefront UAG provides organizations with unparalleled flexibili ... |
|
Register |

|
SYMANTEC CLOUD SOC ADMINISTRATION R2The Cloud SOC R2 Administration course provides an overview of the Cloud SOC service, covering initial setup, deployment options and service configuration. The courseware introduces each topic with an accompanying workfl ... |
|
Register |

|
SYSTEMS SECURITY CERTIFIED PRACTITIONERLooking to move up in the information security field? If you have at least one year of security experience, you qualify for the Systems Security Certified Practitioner (SSCP) certification, which offers junior security p ... |
|
Register |

|
Implementing Cisco Identity Services Engine for Wireless EngineersThis course has been designed to enable wireless engineers understand the concepts, architecture, and use cases of the Cisco Identity Services Engine Solution. This course provides students with the knowledge and skills ... |
|
Register |

|
CYBERSECURITY FOUNDATIONSWhen you consider just a few of the consequences of a security breach - your proprietary information completely accessible, hefty fines for security lapses, news headlines about your company's security breach, it becomes ... |
|
Register |
.jpg)
|
PALO ALTO EXTENDED FIREWALL MANAGEMENT (205)Extended Firewall Management is the next-level follow-on course to Palo Alto Networks® Installation, Configuration, and Management (PAN-EDU-201). Extended Firewall Management expands on 201 course topics, while introduci ... |
|
Register |

|
IBM SECURITY QRADAR SIEM ADVANCED TOPICSThis is an advanced course for the QRadar Analyst and Administrator and is a follow-on to BQ103G. This course uses the IBM QRadar SIEM 7.3 platform for lab exercises. |
|
Register |

|
MASTER CLASS ISO 27001 IMPLEMENTATIONThis five-day intensive course enables the participants to develop the expertise to support an organization in implementing and managing an Information Security Management System (ISMS) as specified in ISO/IEC 27001:2013 ... |
|
Register |

|
CLIENT MANAGEMENT SUITE 8.1 ADMINISTRATIONThe Client Management Suite 8.1 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |

|
IMPLEMENTING ADVANCED CISCO ASA SECURITY V2.0This course provides up-to-date training on the key features of the Cisco ASA 5500-X Series next-Generation Firewall, including ASAv, ASA IDFW, ASA Fire POWER Service Module, ASA Cloud Web Security and ASA Clustering. Ex ... |
|
Register |

|
SECURING CISCO NETWORKS WITH SOURCE FIRE INTRUSION PREVENTION SYSTEMThe Securing Networks with Cisco Firepower Next-Generation IPS course shows you how to deploy and use Cisco Firepower Next-Generation Intrusion Prevention System (NGIPS). This hands-on course gives you the knowledge and ... |
|
Register |

|
BLUE COAT CERTIFIED PROXY PROFESSIONALIn the Blue Coat Certified Proxy Professional (BCCPP) course, you will learn to configure your Blue Coat Proxy appliance for high availability and multi-site deployments, advance policy features, web content control, P2P ... |
|
Register |
.jpg)
|
RED HAT IDENTITY MANAGEMENT AND ACTIVE DIRECTORY INTEGRATION WITH EXAM (EX362)This course teaches you skills on the most requested Red Hat Identity Management (IdM) capabilities, including Active Directory trusts, multi-product federation, configuration management with Ansible, integrated certific ... |
|
Register |

|
CONFIGURING AND DEPLOYING A PRIVATE CLOUDThis course equips students with the skills they require to configure and deploy a cloud using Microsoft System Center 2012 R2. Using hands-on labs, students learn the following: - Produce a high-level design that acc ... |
|
Register |

|
EC-COUNCIL CERTIFIED INCIDENT HANDLERThe EC-Council Certified Incident Handler (ECIH) program is designed to provide the fundamental skills to handle and respond to the computer security incidents in an information system. The course addresses various under ... |
|
Register |

|
CISCO ASA EXPRESS SECURITY 1.5This course has been designed to provide an understanding of Cisco's ASA solution portfolio. Students will learn how to successfully configure various aspects of the Cisco ASA components including Cisco ASA firewall feat ... |
|
Register |

|
IMPLEMENTING CISCO THREAT CONTROL SYSTEMSImplementing Cisco Threat Control Solutions is designed to provide security engineers with the knowledge and hands-on experience required to deploy Cisco’s Email Security (ESA); Web Security (CWS, WSA); Advanced Malware ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 15.5 ADMINISTRATIONThe Symantec Data Loss Prevention 15.5 Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands‐on labs inc ... |
|
Register |

|
RED TEAM VS BLUE TEAM CYBERWAR CHALLENGETwo Teams, two different approaches, Red Team vs Blue Team Cyberwar Challenge! The cyber kill chain - reconnaissance, attack planning and delivery, system exploitation, privilege escalation and lateral movement, anomalie ... |
|
Register |

|
CERTIFIED IN THE GOVERNANCE OF ENTERPRISE ITAs technology has become more and more vital to the achievement of business goals and value delivery, enterprise leaders have realized that enterprise governance must be extended to information technology and information ... |
|
Register |

|
CERTIFIED CHIEF INFORMATION SECURITY OFFICEREC-Council’s CCISO Program has certified leading information security professionals around the world. A core group of high-level information security executives, the CCISO Advisory Board, contributed by forming the found ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 15.0 ADMINISTRATIONThe Symantec Data Loss Prevention 15.0 Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands-on labs inc ... |
|
Register |

|
SYMANTEC IDENTITY AND AUTHENTICATION SERVICES R1The Symantec Identity and Authentication Services R1 course is designed for the IT security professional needing to develop an understanding of the principles and use cases behind the Symantec VIP Service and VIP Access ... |
|
Register |

|
EC - COUNCIL CERTIFIED SECURE PROGRAMMERSoftware defects, bugs, and flaws in the logic of the program are consistently the cause for software vulnerabilities. Analysis by software security professionals has proven that most vulnerabilities are due to errors i ... |
|
Register |

|
JUNOS SPACE-SECURITY DIRECTORThis two-day course is designed to provide students with the knowledge required to manage the Junos Space Security Director application and manage devices with that application. Students will gain in-depth knowledge of h ... |
|
Register |

|
SYMANTEC NET BACKUP 7.6.X: ADMINISTRATIONThis Symantec Net Backup 7.6.x: Administration course provides the IT professional with instruction on the functionality of Symantec NetBackup 7.6.1 software. This course covers the general principles of using NetBackup ... |
|
Register |

|
CITRIX ENTERPRISE SECURITY SOLUTIONSLearn to secure your Citrix environment in this hands-on course that encompasses the core Citrix technologies, including Citrix Virtual Apps and Desktops, ADC, Endpoint Management, Content Collaboration and Citrix Cloud. ... |
|
Register |

|
BLUE COAT PACKET SHAPER PROFESSIONALBlue Coat Certified Packet Shaper Administrator (BCPSA) certification or waiver exam; student should have practical experience with the Packet Shaper appliance in the field with a solid understanding of networking and ge ... |
|
Register |

|
IMPLEMENTING AND MANAGING WINDOWS 10This course is designed to provide students with the knowledge and skills required to install and configure Windows 10 desktops and devices in a Windows Server domain corporate environment. These skills include learning ... |
|
Register |

|
SYMANTEC ASSET MANAGEMENT SUITE 8.5 ADMINISTRATIONThe Symantec Asset Management Suite 8.5 Administration course is designed for professionals tasked with using Symantec Asset Management Suite (AMS) to manage their software and hardware resources in their organizations. ... |
|
Register |

|
COMPUTER HACKING FORENSICS INVESTIGATORThe CHFI course will give participants the necessary skills to identify an intruder's footprints and to properly gather the necessary evidence to prosecute. Many of today's top tools of the forensic trade will be taught ... |
|
Register |
United Kingdom , London |
|||
|---|---|---|---|

|
CompTIA Pentest +As organizations scramble to protect themselves and their customers against privacy or security breaches, the ability to conduct penetration testing is an emerging skill set that is becoming ever more valuable to the org ... |
|
Register |

|
ETHICAL HACKING AND COUNTERMEASURES V.10The Certified Ethical Hacker (C|EH v10) program is a trusted and respected ethical hacking training Program that any information security professional will need. Since its inception in 2003, the Certified Ethical Hacker ... |
|
Register |

|
IBM GUARDIUM FOUNDATIONSAre you getting ready to administer database security policies? Learn how to configure Guardium to discover, classify, analyze, protect, and control access to sensitive data. You learn to perform vulnerability assessment ... |
|
Register |

|
EC-COUNCIL CERTIFIED NETWORK DEFENDERCertified Network Defender (CND) is a vendor-neutral, hands-on, instructor-led comprehensive network security certification training program. It is a skills-based, lab intensive program based on a job-task analysis and c ... |
|
Register |

|
SYMANTEC PROXY SG V6.6: BASIC ADMINISTRATIONThe Proxy SG 6.6 Basic Administration course is an introduction to deployment options and management of the individual key features offered using the Proxy SG 6.6 solution. This an introductory course and is designed for ... |
|
Register |
 PREP COURSE.jpg)
|
COMPTIA ADVANCED SECURITY PRACTITIONER (CASP) PREP COURSEYou have experience in the increasingly crucial field of information security, and now you're ready to take that experience to the next level. CompTIA® Advanced Security Practitioner (CASP) (Exam CAS-002) is the course y ... |
|
Register |

|
Implementing Cisco Secure MobilityThis course is designed to prepare network security engineers with the knowledge and skills they need to protect data traversing a public or shared infrastructure such as the Internet by implementing and maintaining Cisc ... |
|
Register |

|
BLUE COAT CERTIFIED SECURITY ANALYTICS PROFESSIONALThe Blue Coat Certified Security Analytics Professional (BCSAP) course designed for participants who want to learn how to use the Blue Coat Security Analytics platform to perform virtually any type of network-based monit ... |
|
Register |
.png)
|
FIREWALL 8.1: OPTIMIZING FIREWALL THREAT PREVENTION (EDU-214)Successful completion of this four-day, instructor-led course will enhance the student’s understanding of how to better configure, manage, and monitor PAN-OS® threat prevention features. The student will get hands-on exp ... |
|
Register |
.jpg)
|
PANORAMA 8.1: MANAGING FIREWALLS AT SCALE (EDU-220)This course will help students to gain in-depth knowledge about how to configure and manage their Palo Alto Networks® Panorama TM management server. Upon completion of this course, administrators should be familiar with ... |
|
Register |

|
IMPLEMENTING CISCO EDGE NETWORK SECURITY SOLUTIONSThis course has been designed to provide students with the knowledge and skills required to implement and manage security on Cisco ASA firewalls, Cisco Routers with the firewall feature set and Cisco Switches. Students w ... |
|
Register |

|
IMPLEMENTING FOREFRONT IDENTITY MANAGER 2010This four-day instructor-led course introduces and explains the features and capabilities of Microsoft Forefront Identity Manager 2010 (FIM), and provides an overview of the solution scenarios that FIM addresses. The cou ... |
|
Register |
.jpg)
|
RED HAT SECURITY: LINUX IN PHYSICAL, VIRTUAL, AND CLOUD WITH EXAM (EX415)Maintaining security of computing systems is a process of managing risk through the implementation of processes and standards backed by technologies and tools. In this course, you will learn about resources that can be u ... |
|
Register |
.jpg)
|
PALO ALTO NETWORKS® TRAPS™ ADVANCED ENDPOINT PROTECTION (PAN-EDU-281)This instructor-led course teaches strategies in defense against advanced threats. Successful completion of this course enables administrators to better understand the threat landscape. Students will learn the use of Pal ... |
|
Register |

|
JUNOS INTRUSION PREVENTION SYSTEM FUNCTIONALITYThe Junos Intrusion prevention System Functionality (JIPS) course is designed to provide an introduction to the Intrusion Prevention System (IPS) feature set available on the Juniper Networks SRX Series Services Gateway. ... |
|
Register |

|
MANAGING ENTERPRISE SECURITY WITH CISCO SECURITY MANAGERThe Managing Enterprise Security with Cisco Security Manager (SSECMGT) course is aimed at providing network security engineers with the knowledge and skills that are needed to configure and deploy Cisco Security Manager. ... |
|
Register |

|
MASTERCLASS: PEN TESTING AND SECURING MOBILE AND WEB APPLICATIONSThe course teaches mobile and web application security concepts, including the techniques on how to attack and how to respond with an appropriate countermeasure implementation. Our course has been developed around profes ... |
|
Register |

|
UNDERSTANDING CISCO CYBER SECURITY FUNDAMENTALSThe Understanding Cisco Cyber security Fundamentals (SECFND) v1.0 course provides you with an understanding of network infrastructure devices, operations and vulnerabilities of the TCP/IP protocol suite, basic informatio ... |
|
Register |

|
Blue Coat Certified Proxy AdministratorThe Blue Coat Certified Proxy SG Professional (BCCPP) Course is intended for IT professionals who wish to master the advance features of the Blue Coat Proxy SG. |
|
Register |

|
SYMANTEC NETBACKUP 7.5: MAINTAIN AND TROUBLESHOOTThe three day Symantec Net Backup Maintain and Troubleshoot course provides the IT professional with instruction on troubleshooting Symantec NetBackup 7.5 software. This course covers general error detection tools and t ... |
|
Register |
.png)
|
PALO ALTO ADVANCED FIREWALL TROUBLESHOOTING (311)Advanced Firewall Troubleshooting is the next-level follow-on course to Palo Alto Networks® Essentials 1: Installation, Configuration, and Management (PAN-EDU-201) and Essentials 2: Extended Firewall Manager (PAN-EDU-205 ... |
|
Register |

|
JUNOS SECURITYThis five-day course covers the configuration, operation, and implementation of SRX Series Services Gateways in a typical network environment. Key topics within this course include: security zones, security policies, Net ... |
|
Register |

|
RHS333-BUNDLE: RED HAT ENTERPRISE SECURITY: NETWORK SERVICES + EX333Red Hat® Enterprise Security: Network Services with Exam is an intensive course that provides 4 days of instruction and labs that show students how to use the latest technologies to secure services. This class advances b ... |
|
Register |

|
NETWORK AND SECURITY MANAGER FUNDAMENTALSThis two-day course discusses the basic operations of Network and Security Manager. Key topics include server and domain administration, device configuration, template creation and management, policy creation and managem ... |
|
Register |

|
CERTIFIED INFORMATION SYSTEMS AUDITORCISA® is a trademark of the Information Systems Audit and Control Association® (ISACA®) More than 60,000 security professionals hold CISA certification, which was awarded the "Best Professional Certification" for 2009 b ... |
|
Register |

|
Certified Cloud Security Professional Certification PreparationAs powerful as cloud computing is for the organization, understanding its information security risks and mitigation strategies is critical. Legacy approaches are inadequate, and organizations need competent, experienced ... |
|
Register |

|
SECURING EMAIL WITH CISCO EMAIL SECURITY APPLIANCEThe Securing Email with Cisco Email Security Appliance (SESA) v3.0 course shows you how to deploy and use Cisco® Email Security Appliance to establish protection for your email systems against phishing, business email co ... |
|
Register |

|
SYMANTEC CONTROL COMPLIANCE SUITE VULNERABILITY MANAGER 12.0 ADMINISTRATIONThe Symantec Control Compliance Suite Vulnerability Manager (CCS-VM) 12.0 Administration Training is designed for the IT security professional tasked with installation, administering, monitoring and reporting on CCS-VM 1 ... |
|
Register |

|
SECURING NETWORKS WITH FIREPOWER THREAT DEFENSE NGFWThe Securing Networks with Cisco Firepower Threat Defense NGFW (FIREPOWER200) course demonstrates the powerful features of Cisco Firepower Threat Defense, including VPN configuration, traffic control, NAT configuration, ... |
|
Register |

|
SYMANTEC DATA LOSS PREVENTION 14.6 ADMINISTRATIONThe Symantec Data Loss Prevention 14.X: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Data Loss Prevention Enforce platform. The hands-on labs i ... |
|
Register |

|
Certified Threat Intelligence AnalystCertified Threat Intelligence Analyst (C|TIA) is a training and credentialing program designed and developed in collaboration with cybersecurity and threat intelligence experts across the globe to help organizations iden ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.5: ADMINISTRATIONThe Symantec Messaging Gateway 10.5: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This three-day, instructor-led, hands-on cl ... |
|
Register |
.jpg)
|
CISCO CCNA SECURITY BOOT CAMP (ACCELERATED)In this course, you will learn how to install, operate, configure, and verify a basic IPv4 and IPv6 network, including configuring a LAN switch, configuring an IP router, managing network devices. You will also learn abo ... |
|
Register |

|
DEV SEC OPS ENGINEERINGA Dev Sec Ops Engineer is an IT Security professional who is skilled at “security as code” with the intent of making security and compliance consumable as a service. A Dev Sec Ops Engineer uses data and security science ... |
|
Register |

|
SYMANTEC CLIENT MANAGEMENT SUITE 8.5 ADMINISTRATIONThe Client Management Suite 8.5 Administration course is designed for professionals tasked with using Symantec’s Client Management Suite (CMS) to manage their software and hardware resources in their organizations. This ... |
|
Register |

|
SECURING CISCO NETWORKS WITH SNORT RULE WRITING BEST PRACTICESSecuring Cisco Networks with Snort Rule Writing Best Practices is a lab-intensive course that introduces students to the open source Snort community and rule-writing best practices. Users focus exclusively on the Snort r ... |
|
Register |

|
NSX-T: INSTALL, CONFIGURE, MANAGEThis five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T™ Data Center environment. This course covers key NSX-T Data Center features and functionality offer ... |
|
Register |
 CERTIFICATION44.jpg)
|
CERTIFIED INTERNET OF THINGS PRACTITIONER (CIOTP) CERTIFICATIONThe Internet of Things (IoT) promises a wide range of benefits for industry, energy and utility companies, municipalities, healthcare, and consumers. Data can be collected in extraordinary volume and detail regarding alm ... |
|
Register |

|
CYBER SEC FIRST RESPONDER: THREAT DETECTION AND RESPONSEThis course covers the duties of those who are responsible for monitoring and detecting security incidents in information systems and networks, and for executing a proper response to such incidents. Depending on the size ... |
|
Register |

|
SECURITY FUNDAMENTALSIn this course, you will be introduced to security concepts for today's business and technology professionals. You will cover layered security philosophy, physical security, Internet security, and wireless security princ ... |
|
Register |

|
IMPLEMENTING CISCO CYBERSECURITY OPERATIONSThis is the second course in Cisco's CCNA Cyber Ops Curriculum and is designed to provide students with an understanding of how a Security Operations Center (SOC) functions and the knowledge required in this environment. ... |
|
Register |

|
DEPLOYING AND MANAGING WINDOWS 10 USING ENTERPRISE SERVICESThis 5-day course provides administrators with the knowledge and skills needed to deploy and manage Windows 10 desktops, devices, and applications in an enterprise environment. Students learn how to plan and implement Wi ... |
|
Register |
|
|
CYBER SEC FIRST RESPONDER™ (CFR) CERTIFICATIONThis course covers network defense and incident response methods, tactics, and procedures are taught in alignment with industry frameworks such as NIST 800-61 r.2 (Computer Security Incident Handling), US-CERT’s NCISP (N ... |
|
Register |

|
TREND MICRO DEEP DISCOVERY TRAINING FOR CERTIFIED PROFESSIONALSTrend Micro™ Deep Discovery Training for Certified Professionals is a three-day, instructor-led training course where participants will learn how to deploy and manage a Trend Micro™ Deep Discovery threat protection solut ... |
|
Register |

|
COMPTIA CSA+ CYBERSECURITY ANALYSTThe CompTIA CSA+ certification is a vendor-neutral credential. The CompTIA CSA+ exam (Exam CS0-001) is an internationally targeted validation of intermediate-level security skills and knowledge. The course has a technica ... |
|
Register |

|
WORKSHOP: WINDOWS SERVER 2019Learn about the new enhanced capabilities of the Windows 2019 starting from server virtualization, storage, software-defined networking, server management and automation, web and application platform, access to informati ... |
|
Register |

|
RED HAT SERVER HARDENINGSecure a Red Hat Enterprise Linux system to comply with security policy requirements Red Hat® Server Hardening (RH413) builds on a student's Red Hat Certified Engineer (RHCE®) certification or equivalent experience to t ... |
|
Register |

|
CONFIGURING JUNIPER NETWORKS FIREWALL/IPSEC VPN PRODUCTSThis course is the first in the Screen OS curriculum. It is a three-day, instructor-led course that focuses on configuration of the Screen OS firewall/virtual private network (VPN) products in a variety of situations, in ... |
|
Register |

|
SECURITY+The Security+ Certification Prep Course provides the basic knowledge needed to plan, implement, and maintain information security in a vendor-neutral format. This includes risk management, host and network security, auth ... |
|
Register |

|
Channel Partner Securing Email with Cisco Email Security ApplianceThis course is designed to help learners understand how to install, configure, and manage the Cisco Email Security Appliance in a small to medium-sized business and enterprise installation. Knowledge application and basi ... |
|
Register |

|
IMPLEMENTING CISCO NETWORK SECURITY V3.0This is a five-day instructor-led course that focuses on the design, implementation and monitoring of a comprehensive security policy, using Cisco IOS security features and technologies. All IOS examples and hands on exp ... |
|
Register |

|
SYMANTEC SECURITY ANALYTICS 7.2.X ADMINISTRATORThe Symantec Security Analytics Administrator course is intended for IT professionals who want to master the fundamentals of the Symantec Security Analytics solution. Hands-On This course includes practical hands-on exe ... |
|
Register |

|
JNCIE-SEC BOOT CAMPThis five-day course is designed to serve as the ultimate preparation for the Juniper Networks Certified Internet Expert—Security (JNCIE-SEC) exam. The course focuses on caveats and tips useful for potential test candida ... |
|
Register |

|
SYMANTEC MESSAGING GATEWAY 10.6 ADMINISTRATIONThe Symantec Messaging Gateway 10.6: Administration course is designed to provide you with the fundamental knowledge to configure and administer the Symantec Messaging Gateway. This two-day, instructor-led, hand son clas ... |
|
Register |

|
PERFORMANCE TUNING AND OPTIMIZING SQL DATABASESThis four-day instructor-led course provides students who manage and maintain SQL Server databases with the knowledge and skills to performance tune and optimize their databases. |
|
Register |

|
SYMANTEC DEPLOYMENT SOLUTION 8.1 ADMINISTRATIONThe Symantec Deployment Solution 8.1: Administration course is designed for the professional tasked with installing, configuring, and managing a Deployment Solution system. This five-day, instructor-led, hands-on course ... |
|
Register |
.jpg)
|
EC-COUNCIL CERTIFIED SOC ANALYST (CSA)The Certified SOC Analyst (CSA) program is the first step to joining a security operations center (SOC). It is engineered for current and aspiring Tier I and Tier II SOC analysts to achieve proficiency in performing entr ... |
|
Register |

|
IMPLEMENTING CISCO UNIFIED COMMUNICATIONS SECURITYThe Implementing Cisco Unified Communications Security (UCSEC) course is designed to provide students with the necessary knowledge and skills to implement security features in a Cisco Unified Communications environment. ... |
|
Register |
Kuwait , Kuwait |
|||
|---|---|---|---|

|
UNDERSTANDING CISCO CYBER SECURITY FUNDAMENTALSThe Understanding Cisco Cyber security Fundamentals (SECFND) v1.0 course provides you with an understanding of network infrastructure devices, operations and vulnerabilities of the TCP/IP protocol suite, basic informatio ... |
|
Register |

|
SYMANTEC SECURITY ANALYTICS 7.2.X PROFESSIONALThe Symantec Security Analytics Professional course is designed for participants who want to learn how to use the Symantec Security Analytics platform to perform virtually any type of network-based monitoring and forensi ... |
|
Register |
Providing services with a high quality that are satisfying the requirements
Appling the specifications and legalizations to ensure the quality of service.
Best utilization of resources for continually improving the business activities.
BTS keen to selects highly technical instructors based on professional field experience
Since BTS was established, it considered a training partner for world class oil & gas institution
1st floor, Incubator Buildingو Masdar City, Abu Dhabi, UAE
Sun to Fri 09:00 AM to 06:00 PM
Contact Us anytime!